VoIP Intrusion Detection
By Name
Course Title
Tutor
Institution
Department
Date
计算机论文代写 Our analysis shows that not every sender-based loss-recovery technique is suitable for real-time interactive VoIP communications.
Abstract
This paper presents analysis VoIP intrusion detection as well as the techniques suitable for the real-time interactive VoIP communication systems. The paper is basically a proposal that is based on previous studies regarding the same topic. In the paper, it is well provided that effective communication over VoIP is a necessity in the contemporary economy because of the technology’s advantages and benefits over the traditional telephony communication systems. It is also pointed out that its popularity and the advanced features of the VoIP technology as well as the associated benefits encourage security threats to companies using VoIP communication systems. Hackers are thus highly attracted by the new technology in an attempt to take advantage of its growth and popularity for personal benefits.
and its features may seemingly attack the attention of hackers as depicted in the paper. In the case of any issues related to data loss or any other related issues, sender-based loss-recovery techniques are used. Nevertheless, the analysis shows that not each of these techniques is suitable for real-time interactive VoIP communications. Previous studies are consulted to strengthen the analysis results. Intervening technique is found to has no impact in achieving consistent improvement within an environment of lost packets. On the contrary other systems such as peer-to-peer VoIP systems are found to have a significant potential for a wide-spread deployment. The research opens way into studying how to detect Spam in VoIP systems. To enhance successful future implementation of the program, the OPNET 14 Software will be used to construct various simulation scenarios.
译文:
摘要 计算机论文代写
本文介绍了分析 VoIP 入侵检测以及适用于实时交互式 VoIP 通信系统的技术。该论文基本上是基于先前关于同一主题的研究的提案。在本文中,由于 VoIP 技术相对于传统电话通信系统的优势和优势,因此在当代经济中,有效的 VoIP 通信是必不可少的。它还指出,VoIP 技术的普及和先进功能以及相关的好处鼓励使用 VoIP 通信系统的公司的安全威胁。黑客因此被新技术高度吸引,试图利用其增长和普及来谋取个人利益。
正如论文中所描述的那样,它的功能似乎会引起黑客的注意。如果出现与数据丢失或任何其他相关问题相关的任何问题,将使用基于发送者的丢失恢复技术。然而,分析表明,并非所有这些技术都适用于实时交互式 VoIP 通信。参考以前的研究以加强分析结果。发现干预技术对在丢失数据包的环境中实现一致的改进没有影响。相反,其他系统如对等 VoIP 系统被发现具有广泛部署的巨大潜力。该研究为研究如何检测 VoIP 系统中的垃圾邮件开辟了道路。为促进该程序在未来的成功实施,将使用 OPNET 14 软件构建各种模拟场景。
Contents
Abstract …………………………………………………………………………………………………………1
1.0 INTRODUCTION ………………………………………………………………………………………..3
2.0 LITERATURE REVIEW ………………………………………………………………………………6
VoIP techniques ……………………………………………………………………………………………….7
VoIP quality of service issues …………………………………………………………………………….8
3.0 CONCLUSION ……………………………………………………………………………………………9
4.0 BIBLIOGRAPHY ……………………………………………………………………………………….11
1.0 INTRODUCTION
1.1Overview
VoIP is basically an acronym for Voice over IP. It is a methodological approach as well as a technologies for delivering multimedia sessions and voice communications over Internet Protocol (IP) networks like the Internet. It can as well be considered as a group of products, which enable advanced communication services usually over data networks (Keromytis, 2012).
VoIP refers to a class of products that enable advanced
communication services over data networks. While voice is
The technology is today emerging as a substitute to the traditional telephone systems and the associated technologies. The invention of this new technology and its benefits has greatly contributed to its growth. The same factors are now contributing to increased hacking problems within the industry. This problem had not however hindered its ever-increasing popularity and deployment. As this goes on, users suffer various problems associated with VoIP threats from various protocol layers. 计算机论文代写
Session Initiation Protocol is a core protocol for coming real time communication networks, including VoIP, IMS and IPTV networks. Based on the open IP stack, it is similarly susceptible to Denial-of-Service Attacks launched against SIP servers. More than 20 different research works have been published to address SIP-related DoS problems. In thissurvey we explain three different types of DoS attacks on SIP networks, called SIP message payload tampering, SIP message flow tampering and SIP message flooding. We survey different approaches to counter these three types of attacks. We show that there are possible solutions for both payload and flow tampering attacks, and partial solutions for message flooding attacks. We conclude by giving hints how open flooding attacks issues could be addressed.
译文:
1.0 介绍 计算机论文代写
1.1 概述
VoIP 基本上是 IP 语音的首字母缩写词。它是一种方法论方法,也是一种通过互联网协议 (IP) 网络(如互联网)提供多媒体会话和语音通信的技术。它也可以被视为一组产品,通常通过数据网络提供高级通信服务(Keromytis,2012 年)。
VoIP 是指一类能够实现高级
数据网络上的通信服务。虽然声音是
如今,该技术正在成为传统电话系统和相关技术的替代品。这项新技术的发明及其好处极大地促进了其发展。同样的因素现在正在导致行业内黑客问题的增加。然而,这个问题并没有阻碍其不断增长的普及和部署。随着这种情况的发展,用户会遇到与来自各种协议层的 VoIP 威胁相关的各种问题。
会话发起协议是即将到来的实时通信网络的核心协议,包括 VoIP、IMS 和 IPTV 网络。基于开放的 IP 堆栈,它同样容易受到针对 SIP 服务器发起的拒绝服务攻击。已经发表了 20 多项不同的研究工作来解决与 SIP 相关的 DoS 问题。在本调查中,我们解释了对 SIP 网络的三种不同类型的 DoS 攻击,称为 SIP 消息负载篡改、SIP 消息流篡改和 SIP 消息泛洪。我们调查了应对这三种类型攻击的不同方法。我们展示了有效载荷和流量篡改攻击的可能解决方案,以及消息泛洪攻击的部分解决方案。我们最后给出了如何解决开放式泛洪攻击问题的提示。
Malicious attackers may exploit the misconfiguration of devices, the vulnerability of the underlying operating systems, and protocol implementation flaws to break in.
Well-known attacks of data networks such as worms, viruses, Trojan horse, denial-of-service (DoS) attacks can also plague VoIP network devices. It is claimed that 91% of advanced attack evade and affect network systems [1]. The DoS attacks mainly include Signaling DoS attacks, media DoS attacks, and physical DoS attacks [15].
An Intrusion Detection System (IDS) helps administrators to monitor and defend against security breaches. Intrusion detection techniques are generally divided into two paradigms, anomaly detection and misuse detection Voice over Internet Protocol (also called VoIP, IP telephony, Internet telephony and Digital Phone) is the routing of voice conversation over the Internet or any other IP-based network. 计算机论文代写
The voice data flows over a general-purpose packet-switched network, instead of traditional dedicated circuit-switched voice transmission lines. Typically, Intrusion Prevention System may be used as an extension of the IDS for an effective protection model by helping prevent malicious attacks [15]. The components of protection model include a Sip server (Asterisk 10.0.0), IDS (Snort 2.9.1), traffic generator (SIPp 3.1), OS (Debian 6.0.2 SIPp), and a free Open Source test tool or traffic generator [15]. It also include free open source network intrusion detection and prevention system. Figure 1 shows the structure of the protective model.
译文:
恶意攻击者可能会利用设备的错误配置、底层操作系统的漏洞和协议实施漏洞进行入侵。
众所周知的数据网络攻击,例如蠕虫、病毒、特洛伊木马、拒绝服务 (DoS) 攻击,也可能困扰 VoIP 网络设备。据称,91% 的高级攻击会规避和影响网络系统 [1]。 DoS 攻击主要包括信令 DoS 攻击、媒体 DoS 攻击和物理 DoS 攻击[15]。
入侵检测系统 (IDS) 可帮助管理员监控和防御安全漏洞。入侵检测技术通常分为两种范式,异常检测和误用检测互联网协议语音(也称为 VoIP、IP 电话、互联网电话和数字电话)是通过互联网或任何其他基于 IP 的网络进行语音对话的路由。
语音数据流经通用分组交换网络,而不是传统的专用电路交换语音传输线路。通常,入侵防御系统可以用作 IDS 的扩展,通过帮助防止恶意攻击来实现有效的保护模型 [15]。保护模型的组件包括 Sip 服务器(Asterisk 10.0.0)、IDS(Snort 2.9.1)、流量生成器(SIPp 3.1)、OS(Debian 6.0.2 SIPp)和免费的开源测试工具或流量生成器[15]。它还包括免费的开源网络入侵检测和预防系统。图 1 显示了保护模型的结构。
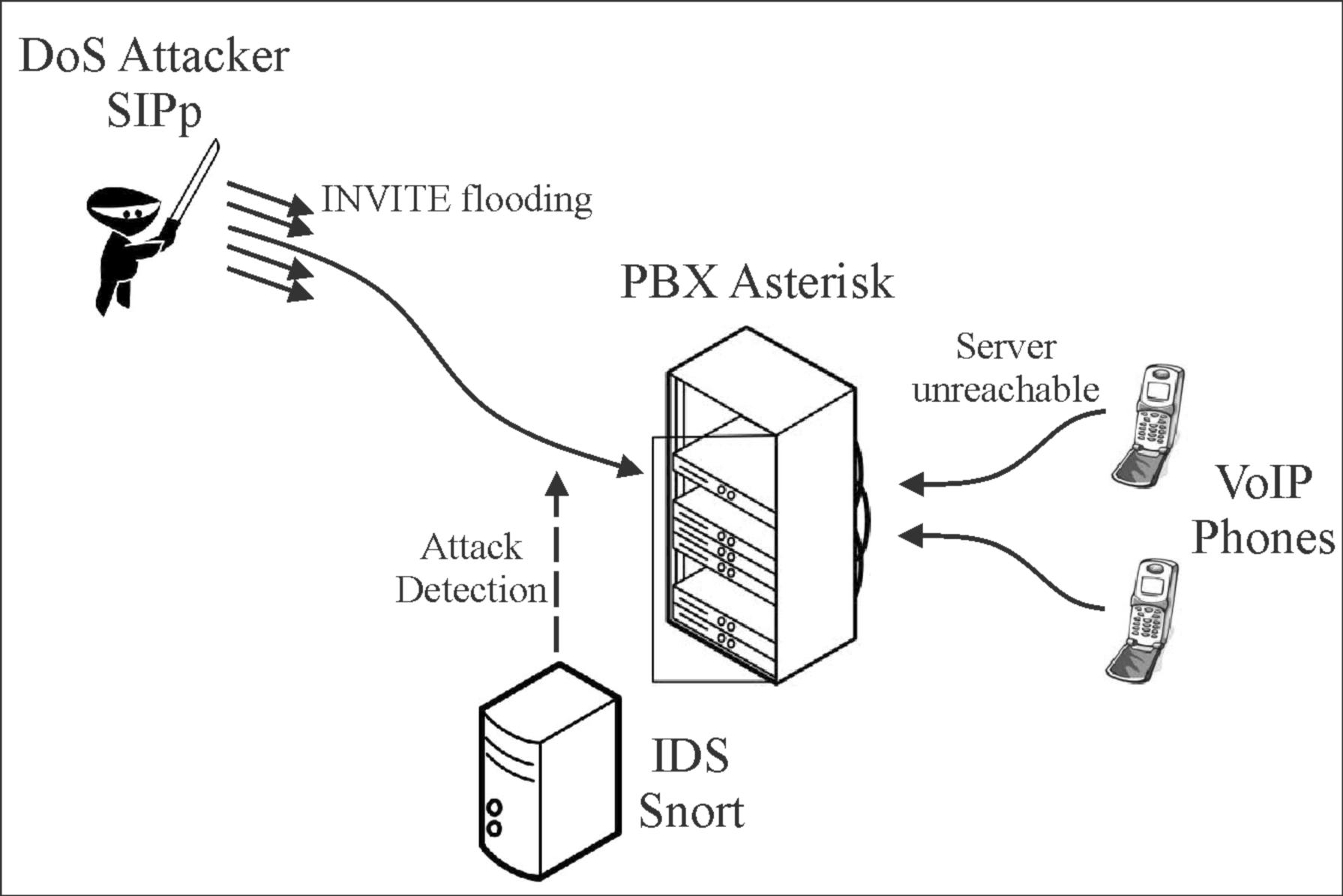
Figure 1: Protection Model
1.2Background 计算机论文代写
1.2.1Motivation
The VoIP is attributed to a number of advantages. Some of the advantages of VoIP include toll bypass, network consolidation and service convergence. Thousands of dollars are saved for large enterprises by placing long distance calls over an IP network instead of traditional telephone system. Network consolidation enables the transmission of data, voice, and video over one single network. The integration greatly reduces setup and maintenance costs. With service convergence, enhanced functionality can be implemented through coupling of multimedia services [2].
The deployment rate of VoIP is increasing steadily. According to Juniper Research, the rapid growth of the global VoIP market will contribute $18 billion in revenues by 2010 [3]. Securing VoIP system is more challenging than securing pure data network. First, all security problems related with data network appear in VoIP system since they share same network infrastructure. Secondly, VoIP does not have a dominant standard so far. The support of two standards in products just increases the chance of buggy application. Dozens of proprietary protocols make the matter worse. Thirdly, the QoS (Quality of Service) requirement of VoIP leaves less working room for possible security measures. A very secure VoIP system that cannot deliver good voice quality is not attractive.
译文:
1.2背景 计算机论文代写
1.2.1 动机
VoIP 具有许多优点。 VoIP 的一些优势包括长途绕行、网络整合和服务融合。通过 IP 网络而非传统电话系统拨打长途电话可为大型企业节省数千美元。网络整合支持通过一个网络传输数据、语音和视频。这种集成大大降低了设置和维护成本。随着服务融合,增强的功能可以通过多媒体服务的耦合来实现[2]。
VoIP 的部署率正在稳步提高。据 Juniper Research 称,全球 VoIP 市场的快速增长到 2010 年将贡献 180 亿美元的收入 [3]。保护 VoIP 系统比保护纯数据网络更具挑战性。首先,所有与数据网络相关的安全问题都出现在VoIP系统中,因为它们共享相同的网络基础设施。其次,到目前为止,VoIP 还没有一个主导标准。产品中两种标准的支持只会增加错误应用的机会。数十种专有协议使情况变得更糟。第三,VoIP 的 QoS(服务质量)要求为可能的安全措施留下了较少的工作空间。一个不能提供良好语音质量的非常安全的 VoIP 系统是没有吸引力的。
1.2.2Problem
Although VoIP is already widely implemented, the technology is far from mature. There is not a dominant protocol standard in the markets. Every vendor uses either its own proprietary or one of two standards, H.323 and SIP (Session Initiation Protocol). For example, Cisco uses the SCCP (Signaling Connection Control Part) protocol, Avaya uses the H.323 protocol with proprietary extensions and Nortel uses the UNISTIM (Unified Network Stimulus) protocol. Proprietary protocols make it difficult to inter-connect products from different vendors.
Good news is that more and more vendors begin to support H.323 or SIP. VoIP transfer voice signal over IP based network. First, human voice needs to be converted to digital bits and encapsulated in packets, which are transmitted using IP network and converted back to voice signal at the destination. Secondly, there should be a way to identify each entity in the network like phone number in traditional telephone system. Thirdly, VoIP entities need to be able to communicate with telephones of PSTN. Generally, implementation, the OPNET 14 Software could be necessary for successful implementation in order to reflect a way of solving the reflected problems and achieve possible advantages of VoIP against the traditional PSTN [16].
译文:
1.2.2问题
尽管 VoIP 已经广泛实施,但该技术还远未成熟。市场上没有占主导地位的协议标准。每个供应商都使用自己的专有标准或两种标准之一,H.323 和 SIP(会话发起协议)。例如,Cisco 使用 SCCP(信令连接控制部分)协议,Avaya 使用带有专有扩展的 H.323 协议,Nortel 使用 UNISTIM(统一网络激励)协议。专有协议使来自不同供应商的产品难以互连。
好消息是越来越多的厂商开始支持 H.323 或 SIP。 VoIP 通过基于 IP 的网络传输语音信号。首先,人的语音需要转换为数字比特并封装在数据包中,通过IP网络传输并在目的地转换回语音信号。其次,应该有一种方法来识别网络中的每个实体,如传统电话系统中的电话号码。第三,VoIP 实体需要能够与 PSTN 的电话进行通信。一般来说,实施,OPNET 14 软件可能是成功实施所必需的,以反映解决所反映问题的方式并实现 VoIP 相对于传统 PSTN 的可能优势 [16]。
1.2.3Description
Generally, there are four major problems associated with VoIP instruction detection. These problems include confidentiality threats, eavesdropping of phone conversation, unauthorized access attacks, and cell redirection or hijacking. Each of these problems is describe below.
译文:
1.2.3 说明
一般来说,VoIP指令检测有四个主要问题。 这些问题包括机密性威胁、电话通话窃听、未经授权的访问攻击以及小区重定向或劫持。 下面描述了这些问题中的每一个。
Confidentiality threats
Confidentiality implies that any given information cannot be accessed by unauthorized parties. The confidential in formation of end users includes private documentation, financial information, and security information like password, conversion content, conversion history or pattern among others. The confidential information for network components includes operation systems, IP addresses, protocols used address mapping, and user records among others. Leak of this information might make attackers’ jobs easier.
译文:
保密威胁
机密性意味着未经授权的各方无法访问任何给定的信息。 最终用户的机密信息包括私人文件、财务信息和安全信息,如密码、转换内容、转换历史或模式等。 网络组件的机密信息包括操作系统、IP 地址、协议使用的地址映射和用户记录等。 泄露这些信息可能会使攻击者的工作变得更容易。
Eavesdropping of phone conversation
Conventional telephone eavesdropping requires either physical access to tap a line, or penetration of a switch. With VoIP, opportunities for eavesdroppers increase dramatically because of the large number of nodes in the path between two conservation entities. If the attacker compromises any of these nodes, he can access the IP packets flowing through that node. There are many free network analyzers and packet capture tools that can convert VoIP traffic to wave files [4]. These tools allow the attackers to save the conversation into the files and play them back on a computer. VoMIT or Voice over Misconfigured Internet Telephones is an example of such a tool [5]. Ethreal can also be used to record SIP packets and retrieve voice message in wav file format. 计算机论文代写
译文:
窃听电话交谈
传统的电话窃听需要物理访问以窃听线路,或穿透交换机。 使用 VoIP,由于两个保护实体之间的路径中有大量节点,窃听者的机会急剧增加。 如果攻击者破坏了这些节点中的任何一个,他就可以访问流经该节点的 IP 数据包。 有许多免费的网络分析器和数据包捕获工具可以将 VoIP 流量转换为波形文件 [4]。 这些工具允许攻击者将对话保存到文件中并在计算机上播放。 VoMIT 或 Voice over Misconfigured Internet Telephones 是此类工具的一个示例 [5]。 Ethreal 还可用于记录 SIP 数据包和检索 wav 文件格式的语音消息。

Unauthorized access attack
Unauthorized access implies that the attacker(s) can access resources on a network that they do not have the authority. Shawn Merdinger reported multiple undocumented ports and services in certain VoIP phones [6]. There are also vulnerabilities due to implementation issues such the lack of familiarity [7].
There are systems for call control, administration, billing and other voice telephone functions. Repositories in these systems may contain passwords, user identities, phone numbers, and private personal information. Lots of gate ways and switches are shipped with default well-known passwords. If these passwords are left without changes, the attacker scan easily break in. Some switches still use TELNET for remote access. The clear-text protocol exposes everything to anyone who can sniff the network traffic. Some of the gate ways or switches might have a web server interfaces for remote control. The attacker might sniff the HTTP traffic in local network to steal sensitive information. Attacker scan also use ARP cache poisoning to forward all traffic through their machines to capture network traffic [17]. 计算机论文代写
Encryption of voice message packets can protect against eavesdropping. IPSec can be deployed to encrypt whole packets. SRTP can provide confidentiality, message authentication and replay protection for audio and video streams. To better protect gateways and switches, they should use SSH instead of other clear-text protocols as remote access protocol. If web-based interface is provided, HTTPS should replace HTTP. In addition, all default passwords should be changed before the system is plugged into the network.
译文:
未经授权的访问攻击
未经授权的访问意味着攻击者可以访问他们没有权限的网络上的资源。 Shawn Merdinger 报告了某些 VoIP 电话中有多个未记录的端口和服务 [6]。由于不熟悉等实施问题,也存在漏洞[7]。
有用于呼叫控制、管理、计费和其他语音电话功能的系统。这些系统中的存储库可能包含密码、用户身份、电话号码和私人个人信息。许多网关和开关都带有默认的众所周知的密码。如果这些密码保持不变,攻击者扫描很容易闯入。一些交换机仍然使用TELNET 进行远程访问。明文协议向可以嗅探网络流量的任何人公开所有内容。某些网关或交换机可能具有用于远程控制的 Web 服务器接口。攻击者可能会嗅探本地网络中的 HTTP 流量以窃取敏感信息。攻击者扫描还使用 ARP 缓存中毒来转发所有流量通过他们的机器来捕获网络流量 [17]。
语音消息包的加密可以防止窃听。可以部署 IPSec 来加密整个数据包。 SRTP 可以为音频和视频流提供机密性、消息认证和重放保护。为了更好地保护网关和交换机,他们应该使用 SSH 而不是其他明文协议作为远程访问协议。如果提供基于 Web 的界面,则 HTTPS 应替换 HTTP。此外,在系统插入网络之前,应更改所有默认密码。
An up-to-date intrusion detection system might detect ARP poisoning and other types of attacks [17].
Integrity of information means that information remains unaltered by unauthorized users. A legitimate user may perform an incorrect or unauthorized operations function and may cause delirious modification, destruction, deletion or disclosure of switch software and data. An intruder may masquerade as a legitimate user and access an operation port of the switch. Registration hijacking happens when an attacker replace the legitimate registration of the victim with his address. The attack causes all incoming calls for the victim to be sent to the attacker’s address. 计算机论文代写
Proxy impersonation attack tricks the victim into communicating with a rogue proxy set up by the attacker. Once an attacker impersonates a proxy, he has complete control of the call. Figure 8 illustrates proxy impersonation. The attacker tricks Alice to communicate with the rogue proxy server instead of the legitimate proxy server [16]. The UAs and proxies normally communicate using UDP and do not require strong authentication to communicate with another proxy. The attack can work by several means, including DNS (Domain Name Service) spoofing, ARP (Address Resolution Protocol) cache spoofing, DHCP spoofing, or changing proxy address for a SIP phone.
译文:
最新的入侵检测系统可能会检测到 ARP 中毒和其他类型的攻击 [17]。
信息的完整性意味着信息不会被未经授权的用户更改。合法用户可能会执行不正确或未经授权的操作功能,并可能导致交换机软件和数据的恶意修改、破坏、删除或泄露。入侵者可以伪装成合法用户访问交换机的操作端口。当攻击者用他的地址替换受害者的合法注册时,就会发生注册劫持。攻击导致受害者的所有来电都被发送到攻击者的地址。
代理模拟攻击诱使受害者与攻击者设置的流氓代理进行通信。一旦攻击者冒充代理,他就可以完全控制呼叫。图 8 说明了代理模拟。攻击者欺骗 Alice 与流氓代理服务器而不是合法代理服务器进行通信 [16]。 UA 和代理通常使用 UDP 进行通信,不需要强身份验证即可与另一个代理进行通信。攻击可以通过多种方式进行,包括 DNS(域名服务)欺骗、ARP(地址解析协议)缓存欺骗、DHCP 欺骗或更改 SIP 电话的代理地址。
Call redirection or hijacking
Call redirection happens whenever calls are intercepted and rerouted through different paths before getting to the destination. Potential methods in this regard include proxy impersonation as well as registration spoofing. The attackers could spoof the response mainly from the call recipient and then trick the call requestor into talking with the attacker. Three classes of protection goals basically exist although also other classifications are possible. The first, which is also the most intuitive class in this case, is confidentiality. This refers to the protection against unwanted disclosure of information.
Confidentiality could be additionally subdivided into data confidentiality, which implies to keeping the secrecy of payload data; confidentiality of the identity of the data’s owner, which refers to anonymity; confidentiality of the pure communication fact; and confidentiality of network structure. The goals here are meant to eliminate or at least minimize the issues of confidentiality, availability, and integrity [8]. Anonymity of a given entity against its communication partner or the communication partners against any third parties could be required.
译文:
呼叫重定向或劫持
每当呼叫在到达目的地之前被拦截并通过不同路径重新路由时,就会发生呼叫重定向。这方面的潜在方法包括代理模拟和注册欺骗。攻击者可以欺骗主要来自呼叫接收者的响应,然后诱使呼叫请求者与攻击者通话。尽管其他分类也是可能的,但基本上存在三类保护目标。第一个,在这种情况下也是最直观的类别,是机密性。这是指防止不必要的信息泄露。
机密性还可以细分为数据机密性,这意味着保持有效载荷数据的机密性;数据所有者身份的保密性,即匿名性;纯通信事实的保密性;和网络结构的保密性。这里的目标旨在消除或至少最小化机密性、可用性和完整性问题 [8]。可能需要给定实体对其通信伙伴或通信伙伴对任何第三方匿名。
A more specific subclass is the confidentiality of the pure fact of communication.
It means that an outside observer is not aware that communication is taking place at all. The fourth subclass, confidentiality of the network structure, is due to the fact that network providers want to conceal properties of their own network such as size, topology, and number of connected customers/nodes, host names, network types, network capacity, availability from competitors while still being able to exchange data and allow roaming. The second major class is integrity of data [8]. Assuring integrity of data means guaranteeing that data is not deleted or replaced along the communication path. Prevention of unauthorized modification of data is called strong integrity protection whereas weak integrity protection only ensures that modifications can be detected. Integrity may also refer to the identities of a communication partner [8]. 计算机论文代写
Assuring integrity of identity means making it impossible for an attacker to use a fake address and masquerade as someone else. Otherwise, it would be possible that confidential data is sent to the attacker instead of the intended recipient. This in turn leads to a violation of the protection goal of data confidentiality. Using a fake identity, also known as spoofing, is difficult in PSTN but common in IP based networks. The third class is security requirements concerning availability. The attacks against availability are known as Denial of Service (DoS).
译文:
一个更具体的子类是纯通信事实的机密性。
这意味着外部观察者根本不知道正在发生通信。第四个子类,网络结构的机密性,是由于网络提供商想要隐藏他们自己网络的属性,例如大小、拓扑和连接的客户/节点的数量、主机名、网络类型、网络容量、可用性来自竞争对手,同时仍然能够交换数据并允许漫游。第二个主要类别是数据的完整性 [8]。保证数据的完整性意味着保证数据不会沿通信路径被删除或替换。防止未经授权的数据修改称为强完整性保护,而弱完整性保护仅确保可以检测到修改。完整性也可以指通信伙伴的身份[8]。
确保身份的完整性意味着使攻击者无法使用虚假地址并伪装成其他人。否则,机密数据可能会发送给攻击者而不是预期的接收者。这反过来又会导致违反数据机密性的保护目标。使用虚假身份(也称为欺骗)在 PSTN 中很困难,但在基于 IP 的网络中很常见。第三类是关于可用性的安全要求。针对可用性的攻击称为拒绝服务 (DoS)。
Such an attack in a PSTN may be the physical disconnection of a network or power cable, gaining administrator access and shutting down the system or deleting files, etc.
In case of IP based networks, the above mentioned and also numerous other DoS attacks are possible. An example would be degrading a service such as VoIP by sending a great number of forged requests to key network elements, e.g. the call processing server. Generally, some integrated security solutions in SIP can be employed to solve some noticeable threats [14]. Table 1 shows possible threats and their corresponding integrated security solutions in SIP.
Table 1: Integrated Security Solutions in SIP
| Threat | Security Solution |
| Call hijacking/man in the middle | Authentication mechanisms |
| Tampering the audio or the signaling | Integrity and non repudiation
mechanisms |
| Eavesdropping | Encryption mechanisms |
译文:
PSTN 中的此类攻击可能是物理断开网络或电源线、获得管理员访问权限并关闭系统或删除文件等。
在基于 IP 的网络的情况下,上述以及许多其他 DoS 攻击都是可能的。 一个例子是通过向关键网络元素发送大量伪造请求来降低 VoIP 等服务的质量,例如 呼叫处理服务器。 通常,可以采用 SIP 中的一些集成安全解决方案来解决一些明显的威胁 [14]。 表 1 显示了 SIP 中可能的威胁及其相应的集成安全解决方案。
表 1:SIP 中的集成安全解决方案
| Threat | Security Solution |
| Call hijacking/man in the middle | Authentication mechanisms |
| Tampering the audio or the signaling | Integrity and non repudiation
mechanisms |
| Eavesdropping | Encryption mechanisms |
2.0 LITERATURE REVIEW
2.1Overview
In the curse of designing security mechanisms one has to determine the degree at which every security requirements has to be fulfilled. This aspect depends on the attack types and the profile of the attacker. Different types of attackers are known to have different motives for performing attacks. The attacker could be a student with a goal of having fun snooping on people’s e-mails, crackers test out people’s security systems, ex-employees getting revenge for having been fired, or even spies learning enemies military or industrial secrets among others [9].
Regarding types of attacks, they may be classified in two broad ways [10]. The first way being to distinguish between passive attacks and active attacks whereby a “passive attack” would refer to an attempt to learn or make use of information obtained from the system, although it does not affect any system resources. On the other hand an “active attack”, tries to modify system resources or even affect their operation. Active attacks mainly include interruption of services, modification of messages, fabrication of messages, and replay to attacks. 计算机论文代写
The latter implies to the recording of legitimate messages and sending them again and again mainly to the recipients [10]. In order to achieve a predetermined protection goal different protection mechanisms are applied. Confidentiality of data is achieved by installing network components specifically in physically secure environments or even by using encryptions. Encryption may be used for providing data confidentiality and for protecting data integrity through means of hash values, Message Authentication Code (MAC) or digital signatures.
译文:
2.0 文学评论 计算机论文代写
2.1 概述
在设计安全机制的诅咒中,必须确定必须满足每个安全要求的程度。这方面取决于攻击类型和攻击者的个人资料。众所周知,不同类型的攻击者具有不同的执行攻击动机。攻击者可能是一名学生,其目标是窃取人们的电子邮件,破解者测试人们的安全系统,前雇员因被解雇而报复,甚至间谍了解敌人的军事或工业机密等 [9] .
关于攻击的类型,它们可以分为两大类 [10]。第一种方法是区分被动攻击和主动攻击,其中“被动攻击”是指尝试学习或利用从系统获得的信息,尽管它不影响任何系统资源。另一方面是“主动攻击”,试图修改系统资源甚至影响其运行。主动攻击主要包括服务中断、消息修改、消息制作和重放攻击。
后者意味着记录合法消息并一次又一次地将它们发送给接收者[10]。为了实现预定的保护目标,应用了不同的保护机制。数据的机密性是通过在物理安全环境中专门安装网络组件或什至使用加密来实现的。加密可用于通过散列值、消息验证码 (MAC) 或数字签名来提供数据机密性和保护数据完整性。
2.2 Types of Attacks in Communication Networks
An important issue for achieving most protection goals is providing access control, i.e. allowing only authorized users to gain access to the system. Therefore, first the identity of the user requesting access has to be verified which is called authentication. Then the request, e.g. placing a telephone call, is used together with the user ID and a policy database to check whether the user should be granted or rejected access to the system. This is called authorization. A related issue is accounting, i.e. requiring payment from the user according to the service used. Authentication, authorization and accounting mechanisms, known as AAA, are an essential part of every communication network, including ISDN, GSM, UMTS and IP based networks [15]. 计算机论文代写
Implementing the security mechanisms introduced in this case can be done on each layer of the network protocol stack: physical, data link, network, and transport or application layer. Another very important aspect is that even providing a good technical solution is still not sufficient. Giving the opportunity for malicious persons to operate the system on his behalf? In fact, most damage due to successful attacks against security is the result of human mistakes rather than technical weaknesses of the systems [17].
译文:
2.2 通信网络中的攻击类型 计算机论文代写
实现大多数保护目标的一个重要问题是提供访问控制,即只允许授权用户访问系统。因此,首先必须验证请求访问的用户的身份,这称为身份验证。然后是请求,例如拨打电话,与用户 ID 和策略数据库一起使用,以检查是否应授予或拒绝用户访问系统。这称为授权。一个相关的问题是会计,即根据所使用的服务要求用户付款。身份验证、授权和计费机制,称为 AAA,是每个通信网络的重要组成部分,包括 ISDN、GSM、UMTS 和基于 IP 的网络 [15]。
在这种情况下引入的安全机制可以在网络协议栈的每一层实现:物理层、数据链路层、网络层和传输层或应用层。另一个非常重要的方面是,即使提供良好的技术解决方案仍然是不够的。给恶意的人代表他操作系统的机会?事实上,成功攻击安全造成的大多数损害是人为错误的结果,而不是系统的技术弱点 [17]。
It is typically crucial to make users aware of security issues to minimize this source of security threats.
This is called “social engineering”. It may not be discussed in much detail as this article is focused primarily on the technical side of security but understanding its importance is essential. Therefore, more countermeasures against these and other attacks are necessary. However, stating an important note is appropriate at this place [14]. In practice, no perfect solution for securing a system may be found which is able to prevent all existing (and not yet existing) attacks. 计算机论文代写
Aiming an absolute perfection will inevitably lead to an increase of costs and complexity and will cause much inconvenience for the users interacting with the system. Therefore it is important to find a trade-off between security services, the efforts to provide these services (e.g. equipment, implementation and maintenance costs) and the level of inconvenience that users will experience while interacting with the system due to the additional security services. In order to find this trade-off the designer should first clarify against which attackers the system should offer protection and what means they have for attacking the system. Particularly for the design of an IP Telephony network the following aspects should be considered when searching for an optimal trade-off [11].
译文:
让用户意识到安全问题以最大限度地减少这种安全威胁来源通常至关重要。
这被称为“社会工程”。由于本文主要关注安全性的技术方面,因此可能不会对其进行详细讨论,但了解其重要性至关重要。因此,需要针对这些攻击和其他攻击采取更多对策。然而,在这个地方声明一个重要的注释是合适的[14]。在实践中,可能找不到能够防止所有现有(和尚不存在)攻击的完美系统保护解决方案。
追求绝对完美必然会导致成本和复杂性的增加,并且会给与系统交互的用户带来很多不便。因此,重要的是要在安全服务、提供这些服务的努力(例如设备、实施和维护成本)以及用户在与系统交互时由于额外的安全服务而遇到的不便程度之间进行权衡,这一点很重要。为了找到这种权衡,设计者应该首先阐明系统应该针对哪些攻击者提供保护以及他们有什么手段来攻击系统。特别是对于 IP 电话网络的设计,在寻找最佳权衡 [11] 时应考虑以下方面。
A segmentation of the data and voice is a key issue.
This may seem to be in conflict with the main idea of VoIP which is the integration of voice into an existing IP data network. However, segmentation does not mean that two different IP infrastructures should be deployed: one for voice and one for data. A logical separation in voice and data segments can be done instead by the use of VLANs. 计算机论文代写
For creating a VLAN the layer 2 switches have to be VLAN aware; that is, they should have the required functionality to support VLANs. The network administrator can then assign each device on the network to a certain VLAN. Thereby it should be considered that many IP phones support a data port to allow the connection of a PC to the phone so that only a single cable is necessary to provide data and voice connectivity to the user. Hence, these should also have options to support VLAN. [11].
译文:
数据和语音的分段是一个关键问题。
这似乎与将语音集成到现有 IP 数据网络中的 VoIP 的主要思想相冲突。 然而,分段并不意味着应该部署两种不同的 IP 基础设施:一种用于语音,一种用于数据。 语音和数据段的逻辑分离可以通过使用 VLAN 来完成。
要创建 VLAN,第 2 层交换机必须能够识别 VLAN; 也就是说,它们应该具有支持 VLAN 所需的功能。 然后,网络管理员可以将网络上的每个设备分配到某个 VLAN。 因此,应考虑到许多 IP 电话支持数据端口以允许 PC 连接到电话,因此只需要一根电缆即可为用户提供数据和语音连接。 因此,这些也应该有支持 VLAN 的选项。 [11]。
2.3 VoIP Techniques
Researchers have proposed many techniques for improving quality of service (QoS) in the face of packet loss. Some of these techniques employ receiver-based packet-loss concealment (PLC) approaches. Many audio encoder/decoders use PLC algorithms to synthesize audio when packets of audio data are missing. There are also sender-based loss-recovery techniques, whereby the sender assumes an active role to help the receiver recover lost data or improve Qu’s when packet loss occurs. Commonly, sender-based techniques are independent of receiver-based techniques, so designers can employ both types of loss-recovery methods simultaneously [13].
The choice of any particular audio encoder/decoder (i.e., codec) with PLC transparently provides the degree of receiver-based packet-loss recovery that the selected codec offers. Designers normally consider packet-loss resilience along with several other factors when choosing codecs. Sender-based packet-loss recovery can supplement or even entirely replace receiver-based packet-loss concealment, so designers must also consider sender-based packet-loss recovery as part of the overall design for improving QoS. Most sender-based loss-recovery mechanisms work by retransmitting data or by transmitting additional data [15]. 计算机论文代写
These approaches consume additional resources such as network bandwidth and CPU capacity. The increase in the consumption of network bandwidth puts more loads on the network and can potentially result in the loss of more packets, perhaps ironically exacerbating the very problem we are trying to solve. Sender-based loss-recovery techniques typically introduce added end-to-end delay into the media stream. Generally, humans cannot even perceive a one-way delay of less than 100ms, and most users can tolerate a one-way delay of up to 250ms.If the one-way delay exceeds 250 ms, however, the delay can result in a serious talker-overlap effect that is intolerable for most users [12].
译文:
2.3 VoIP 技术 计算机论文代写
研究人员提出了许多技术来提高服务质量 (QoS) 来应对丢包问题。其中一些技术采用基于接收器的数据包丢失隐藏 (PLC) 方法。当音频数据包丢失时,许多音频编码器/解码器使用 PLC 算法来合成音频。还有基于发送方的丢失恢复技术,其中发送方扮演积极的角色,帮助接收方恢复丢失的数据或在发生丢包时改善 Qu。通常,基于发送方的技术独立于基于接收方的技术,因此设计人员可以同时采用两种类型的丢失恢复方法 [13]。
任何特定音频编码器/解码器(即编解码器)与 PLC 的选择透明地提供了所选编解码器提供的基于接收器的数据包丢失恢复的程度。设计人员在选择编解码器时通常会考虑丢包恢复能力以及其他几个因素。基于发送方的丢包恢复可以补充甚至完全替代基于接收方的丢包隐藏,因此设计人员还必须考虑将基于发送方的丢包恢复作为提高服务质量的整体设计的一部分。大多数基于发送者的丢失恢复机制通过重新传输数据或传输附加数据来工作 [15]。
这些方法会消耗额外的资源,例如网络带宽和 CPU 容量。网络带宽消耗的增加会给网络带来更多负载,并可能导致更多数据包丢失,讽刺的是,这可能会加剧我们正试图解决的问题。基于发送方的丢失恢复技术通常会在媒体流中引入额外的端到端延迟。一般人类连100ms以下的单向延迟都无法感知,大多数用户可以容忍高达250ms的单向延迟。但是如果单向延迟超过250ms,就会导致严重的延迟大多数用户无法忍受的谈话者重叠效应 [12]。
2.3.1 Loss-Recovery Techniques
When trying to combat the effects of packet loss in VoIP systems, designers typically do not use sender-based loss-recovery techniques. One of the main reasons for avoiding sender based loss-recovery techniques is that all of the existing approaches require additional network bandwidth. As the utilization of the data bandwidth increases, the data network becomes more congested and can discard more packets. Consequently, sender-based loss-recovery techniques, which are supposed to improve QoS when packet loss occurs, can actually degrade the audio quality by causing more lost packets [12]. 计算机论文代写
Plain delivery is more prevalent than any other delivery technique in VoIP solutions. Plain delivery does not provide any sender-based effort to improve audio quality when packet loss occurs. We include this approach to provide a baseline for purposes of comparison. This technique simply packages each block of encoded audio data into an IP packet and transmits the packet. For example, if we use a 20 mms frame length; we package 38 bytes of iLBC encoded data into an IP packet for transmission. In the case of G.729A, we package 20 bytes of encoded audio data for a 20 ms period into an IP packet for transmission [12].
译文:
2.3.1 丢失恢复技术
在尝试对抗 VoIP 系统中数据包丢失的影响时,设计人员通常不使用基于发送方的丢失恢复技术。避免使用基于发送者的丢失恢复技术的主要原因之一是所有现有方法都需要额外的网络带宽。随着数据带宽利用率的增加,数据网络变得更加拥塞并且可以丢弃更多数据包。因此,基于发送方的丢失恢复技术本应在发生数据包丢失时提高 QoS,但实际上会导致更多的数据包丢失,从而降低音频质量 [12]。
在 VoIP 解决方案中,普通传送比任何其他传送技术都更为普遍。当发生数据包丢失时,普通传送不提供任何基于发送者的努力来提高音频质量。我们包含此方法以提供用于比较目的的基线。这种技术只是将每个编码的音频数据块打包成一个 IP 数据包并传输该数据包。例如,如果我们使用 20 毫米的框架长度;我们将 38 字节的 iLBC 编码数据打包成一个 IP 包进行传输。在 G.729A 的情况下,我们将 20 毫秒的 20 字节编码音频数据打包成一个 IP 数据包进行传输 [12]。
In either case, we transmit 50 packets per second. If we transmit the packets via Ethernet, the header overhead is 78 bytes per IP packet (12 bytes for the interpacket idle time,
26 bytes for Ethernet overhead including CRC and preamble, 20 bytes for IPv4, 8 bytes for UDP, and 12 bytes for RTP). Consequently, we consume 46.4 kb/s for iLBC and 39.2kb/s for G.729A. Plain delivery introduces 20 ms of delay into the audio stream. Interleaving Interleaving [13] is not really a loss-recovery technique, since this approach is not able to recover any lost data despite its importance [10]. However, this method attempts to reduce the degradation of perceptual audio quality by distributing lost data into several small gaps instead of having one large gap of lost data. 计算机论文代写
Many researchers believe that listeners can mentally patch over a loss more easily if we disperse the loss into several small parts. Since this technique does not transmit additional information, it requires the same bandwidth utilization that plain delivery uses. Interleaving is feasible only if we transmit multiple frames of audio in each IP packet [11]. If we packaged two frames of audio into one IP packet, we would transmit packets of interleaved audio frames, as Fig. 1 illustrates. We could further scatter lost frames by interleaving more frames into each IP packet. Figure 2 illustrates interleaving with four audio frames per IP packets.
译文:
在任何一种情况下,我们每秒传输 50 个数据包。如果我们通过以太网传输数据包,每个 IP 数据包的头部开销是 78 字节(数据包间空闲时间为 12 字节,
26 字节用于以太网开销,包括 CRC 和前导码,20 字节用于 IPv4,8 字节用于 UDP,12 字节用于 RTP)。因此,我们为 iLBC 消耗 46.4 kb/s,为 G.729A 消耗 39.2kb/s。普通传送会在音频流中引入 20 毫秒的延迟。交错交错 [13] 并不是真正的丢失恢复技术,因为尽管这种方法很重要 [10],但它无法恢复任何丢失的数据。然而,这种方法试图通过将丢失的数据分布到几个小间隙而不是一个大的丢失数据间隙来减少感知音频质量的下降。
许多研究人员认为,如果我们将损失分成几个小部分,听众可以更容易地在心理上弥补损失。由于此技术不传输附加信息,因此需要与普通传送使用的带宽利用率相同。只有当我们在每个 IP 数据包中传输多帧音频时,交织才是可行的 [11]。如果我们将两帧音频打包成一个 IP 数据包,我们将传输交错音频帧的数据包,如图 1 所示。我们可以通过将更多帧交织到每个 IP 数据包中来进一步分散丢失的帧。图 2 说明了每个 IP 数据包与四个音频帧的交织。
Increased interleaving provides improved dispersal of lost audio frames, but increased interleaving also introduces a larger delay into the media stream.
Larger delays can cause serious problems such as talker overlap, so interleaving improves some aspects of quality while degrading others. Forward error correction (FEC) is a sender-based technique for mitigating the undesired effects of packet loss. FEC works by transmitting redundant packets for error correction. Reed–Solomon encoding is a well-known block-based error-correction mechanism. Reed-Solomon codes enjoy widespread use in storage applications and digital communications ranging from Compact Disk and DVD to wireless communication, satellite communication, digital television, and high-speed modems [9].
The Reed–Solomon encoding scheme, works by generating parity bits and the sending the parity bits along with the data values. If data values are missing or corrupt, the Reed–Solomon decoder cans reconstruct the original data by using the redundant information from the parity bits. The measure of the redundancy in the block determines the error-correcting ability of the Reed–Solomon code. 计算机论文代写
Reed–Solomon coding can be computationally quite expensive to implement on a general-purpose microprocessor, especially in a real-time software implementation such as VoIP. A router drops packets when it is overloaded, so a router is likely to drop packets that arrive during a busy time. A router that drops the original packet is therefore likely to drop the duplicate packet as well if we transmit the duplicate packet immediately after the original packet [11]. If we delay the transmission of the duplicate packet, we reduce the chance of losing both packets but also need to add this delay into the overall delay that this approach introduces into the audio stream.
译文:
增加的交织提供了对丢失音频帧的改进的分散,但是增加的交织也将更大的延迟引入到媒体流中。
较大的延迟会导致严重的问题,例如讲话者重叠,因此交错改善了某些方面的质量,同时降低了其他方面的质量。前向纠错 (FEC) 是一种基于发送方的技术,用于减轻数据包丢失的不良影响。 FEC 的工作原理是传输冗余数据包以进行纠错。 Reed-Solomon 编码是一种众所周知的基于块的纠错机制。 Reed-Solomon 码广泛用于存储应用和数字通信,从光盘和 DVD 到无线通信、卫星通信、数字电视和高速调制解调器 [9]。
Reed-Solomon 编码方案通过生成奇偶校验位并将奇偶校验位与数据值一起发送来工作。如果数据值丢失或损坏,Reed-Solomon 解码器可以使用奇偶校验位的冗余信息重建原始数据。块中冗余的度量决定了 Reed-Solomon 码的纠错能力。
在通用微处理器上实现 Reed-Solomon 编码在计算上可能非常昂贵,尤其是在 VoIP 等实时软件实现中。路由器在过载时会丢弃数据包,因此路由器很可能会丢弃在繁忙时间到达的数据包。因此,如果我们在原始数据包之后立即传输重复数据包 [11],那么丢弃原始数据包的路由器也可能丢弃重复数据包。如果我们延迟重复数据包的传输,我们会减少丢失两个数据包的机会,但也需要将此延迟添加到该方法引入音频流的整体延迟中。
2.4 VoIP Quality of Service Issues 计算机论文代写
2.4.1Jitter
Jitter refers to non-uniform packet delays. It is often caused by low bandwidth situations in VOIP and can be exceptionally detrimental to the overall QoS. Variations in delays can be more detrimental to QoS than the actual delays themselves. Jitter can cause packets to arrive and be processed out of sequence.
译文:
2.4 VoIP 服务质量问题 计算机论文代写
2.4.1抖动
抖动是指不均匀的数据包延迟。 它通常是由 VOIP 中的低带宽情况引起的,并且可能对整体 QoS 非常不利。 与实际延迟本身相比,延迟的变化对 QoS 的危害更大。 抖动会导致数据包到达并被乱序处理。
2.4.2Latency
Latency in VOIP refers to the time it takes for a voice transmission to go from its source to its destination. Ideally, we would like to keep latency as low as possible but there are practical lower bounds on the delay of VOIP. Packet LosPacket loss is another major QoS issue for VoIP systems. VOIP is exceptionally intolerant of packet loss. Packet loss can result from excess latency, where a group of packets arrives late and must be discarded in favor of newer ones. It can also be the result of jitter, that is, when a packet arrives after its surrounding packets have been flushed from the buffer, making the received packet useless. 计算机论文代写
Administrators must be able to prioritize allocated bandwidth to VoIP traffic to ensure adequate quality of service (QoS). Underperforming firewalls can potentially degrade VoIP communications with latency, jitter, packet loss and echo. The ideal solution would include control over QoS prioritization, comprehensive security that introduces no latency, and secure access to VoIP applications over VPNs. QoS network security appliances provide built-in, security and bandwidth optimization, as well as easy support for VoIP, SIP devices throughout the network. Integrated QoS allows prioritization of VoIP and data traffic on the network.
译文:
2.4.2延迟
VOIP 中的延迟是指语音传输从源到目的地所需的时间。理想情况下,我们希望保持尽可能低的延迟,但 VOIP 的延迟有实际的下限。数据包丢失数据包丢失是 VoIP 系统的另一个主要 QoS 问题。 VOIP 异常不能容忍丢包。数据包丢失可能是由于延迟过大造成的,其中一组数据包延迟到达并且必须被丢弃以支持更新的数据包。它也可能是抖动的结果,即当一个数据包在其周围的数据包从缓冲区中被刷新后到达时,使接收到的数据包变得无用。
管理员必须能够优先为 VoIP 流量分配带宽,以确保足够的服务质量 (QoS)。性能不佳的防火墙可能会因延迟、抖动、数据包丢失和回声而降低 VoIP 通信的性能。理想的解决方案将包括对 QoS 优先级的控制、引入无延迟的全面安全性以及通过 VPN 安全访问 VoIP 应用程序。 QoS 网络安全设备提供内置的安全性和带宽优化,以及对整个网络中的 VoIP、SIP 设备的轻松支持。集成的 QoS 允许对网络上的 VoIP 和数据流量进行优先级排序。
Some of the IDSs are generic in nature and can be customized with detection rules specific to the environment in which they are deployed (e.g., Snort and Prelude Most existing IDS solutions, such as Snort, provide only a generic architecture in which the IDS itself does not pay much attention to the application level protocols and the corresponding state information.
Consequently, the user has to construct detection rules from the ground to capture these application level contexts for performing detection. A traditional IDS like Snort with a rule to detect multiple 4XX responses may flag a large number of false alarms. The Snort IDS is well known for its efficiency in examining incoming packets and SPACEDIVE leverages the Snort functionality. 计算机论文代写
To avoid performance loss, SPACEDIVE is built into Snort using part of its low-level functionality (examining and processing packets) and adding to it (e.g., to build state to support stately detection) and building completely the high level functionality specific to the VoIP environment. The native rule language of Snort is not well-suited for VoIP stateful or cross-protocol detection. Snort provides limited capability for remembering state both within a VoIP session for a given protocol (e.g. SIP) and across protocols (e.g. SIP & RTP). To make up for this, we add constructs to the existing rule language so that it is better-suited for detecting attacks targeted to VoIP environments that span packets in a session and different protocols.
译文:
一些 IDS 本质上是通用的,可以使用特定于它们部署环境的检测规则进行定制(例如,Snort 和 Prelude 大多数现有的 IDS 解决方案,例如 Snort,仅提供 IDS 本身在其中执行的通用架构不太关注应用层协议和相应的状态信息。
因此,用户必须从地面构建检测规则来捕获这些应用程序级上下文以执行检测。像 Snort 这样具有检测多个 4XX 响应规则的传统 IDS 可能会标记大量误报。 Snort IDS 以其检查传入数据包的效率而闻名,而 SPACEDIVE 则利用了 Snort 功能。
为避免性能损失,SPACEDIVE 内置于 Snort 中,使用其部分低级功能(检查和处理数据包)并添加到其中(例如,构建状态以支持状态检测)并完全构建特定于 VoIP 的高级功能环境。 Snort 的本地规则语言不太适合 VoIP 状态或跨协议检测。 Snort 提供了有限的能力来记住给定协议(例如 SIP)和跨协议(例如 SIP 和 RTP)的 VoIP 会话内的状态。为了弥补这一点,我们向现有规则语言添加了结构,使其更适合检测针对跨越会话和不同协议中的数据包的 VoIP 环境的攻击。
3.0 CONCLUSION
Our analysis shows that not every sender-based loss-recovery technique is suitable for real-time interactive VoIP communications. Although previous researchers have reported that interleaving can reduce the degradation of perceptual audio quality, our study shows that the interleaving technique does not achieve any consistent or significant improvement in an environment of lost packets.
Another important area of our ongoing research is that of peer-to-peer VoIP systems. Peer-to-peer VoIP systems have a great potential for wide-spread deployment – an example is the popular Skype system. We are also looking at ways to detect Spam in VoIP systems. Finally, we are investigating the effectiveness of our system in presence of secure protocols. For successful future implementation, the OPNET 14 Software will be used to construct various simulation scenarios. The simulation is to ensure successful implementation in order to reflect the possible advantages of VoIP against the traditional PSTN.
译文:
3.0 结论 计算机论文代写
我们的分析表明,并非所有基于发送方的丢失恢复技术都适用于实时交互式 VoIP 通信。尽管之前的研究人员报告说,交织可以减少感知音频质量的下降,但我们的研究表明,交织技术在丢包的环境中并没有取得任何一致或显着的改善。
我们正在进行的研究的另一个重要领域是点对点 VoIP 系统。点对点 VoIP 系统具有广泛部署的巨大潜力——一个例子是流行的 Skype 系统。我们也在寻找在 VoIP 系统中检测垃圾邮件的方法。最后,我们正在调查我们系统在存在安全协议的情况下的有效性。为了未来的成功实施,OPNET 14 软件将用于构建各种模拟场景。模拟是为了确保成功实施,以反映 VoIP 相对于传统 PSTN 的可能优势。
Concerning the types of attacks these may be classified in two ways. The first way is to distinguish between passive and active attacks.
A “passive attack” is an attempt to learn or make use of information from the system but does not affect system resources an “active attack”, on the other hand, attempts to alter system resources or affect their operation. Active attacks include the interruption of a service, the modification of messages, the fabrication of messages (often with fake source addresses) and replay attacks, i.e. recording a legitimate message and sending it again and again to the recipient. 计算机论文代写
Based on the analysis and consulted literature, it can be pointed out that achievement of protection goals would always required the use of different protection mechanisms. Confidentiality of the data is mostly achievable through installing network components specifically in physically secure environments or it could be achieved by using encryption as explained in the report. The encryption could be applied for providing confidentiality of data as well as in protecting data integrity by means of hash values, Message Authentication Code (MAC) or digital signatures.
译文:
关于攻击的类型,这些可以分为两种方式。第一种方法是区分被动攻击和主动攻击。
“被动攻击”是试图从系统中学习或利用信息但不影响系统资源的“主动攻击”,另一方面,试图改变系统资源或影响其运行。主动攻击包括中断服务、消息的修改、消息的制造(通常带有虚假源地址)和重放攻击,即记录合法消息并一次又一次地将其发送给接收者。
根据分析和查阅文献,可以指出实现保护目标总是需要使用不同的保护机制。数据的机密性主要可以通过在物理安全环境中专门安装网络组件来实现,或者可以通过使用报告中解释的加密来实现。加密可用于提供数据的机密性以及通过散列值、消息验证码 (MAC) 或数字签名保护数据完整性。
4.0 BIBLIOGRAPHY
[1] Aviles, M., 2014. HP TippingPoint: Neutralize ‘Patient Zero’ and stop malicious traffic from spreading on your network. [Online] Available at: http://h30499.www3.hp.com/t5/HP-Security-Products-Blog/HP-TippingPoint-Neutralize-Patient-Zero-and-stop-malicious/ba-p/6605098#.VHZBpM6vNio[Accessed 26 November 2014]. [2] Collier M., 2014. The Current State of VoIP Security. [Online] Available at: http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=0CB8QFjAA&url=http%3A%2F%2Fdownload.securelogix.com%2Flibrary%2FThe_Current_State_of_VoIP_Security.pdf&ei=iEN2VPe2GNK0uASoqoCoBg&usg=AFQjCNFLkpZhP3BsVgiqt3DKfmPqtcFqkw&sig2=KKPWkg3UOkoPw5ObyxP97A [Accessed 26November 2014]. [3] Prabhakar, G.; Rastogi, R.; Thotton, M.,2005. OSS Architecture & Requirements for VoIP Networks. Bell Labs Technical Journal 10 (1): pp.31–45 [4] Roberts, C. 2005. Voice over IP security. Center for critical Infrastructure Protection.* [5] Provost, N. 2006. VOMIT – Voice Over Misconfigured Internet Telephones. [Online] Available at: http://vomit.xtdnet.nl/. [Accessed 26 November 2014]. [6] Merdinger S., 2006. ACT P202S VoIP wireless phone multiple undocumented ports/services. [Online] Available at: http://www.security.nnov.ru/Ldocument66.html. [Accessed 26 November 2014]. [7] Schroder C., 2006. Understand IPv6 Address. [Online] Available at: http://www.enterprisenetworkingplanet.com/netsp/article.php/3633211/Understand-IPv6-Addresses.htm [Accessed 26 November 2014] [8] Batchvarov A., 2004. Security Issues and Solutions for Voice over IP compared to Circuit Switched Networks. [Online] Available at: http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&ved=0CCIQFjAA&url=http%3A%2F%2Fwww.linecity.de%2FINFOTECH_ACS_SS04%2Facs4_top_6.pdf&ei=T0t2VL6QIdGvafa-gdgF&usg=AFQjCNFFWvB9cwvQGNvCASHq5zzJ3jiSMg&sig2=mMmMbFpaDgkNLeJVTN74rg [Accessed 26 November 2014]. [9] Tanenbaum A. S., 2003. Computer networks. Chapter 8, pp. 722, Fourth Edition, Prentice Hall. [10] Shirey R., 2000. Internet Security Glossary. RFC (Informational): 2828, IETF. [Online] Available at: https://www.ietf.org/rfc/rfc2828.txt [Accessed 26 November 2014]. [11] Halpern J., SAFE: IP Telephony Security in Depth. Cisco Systems, White Paper. [Online] Available at: http://tinyurl.com/dtf2h [Accessed 26 November 2014] [12] P. T. Brady, 1971. Effects of Transmission Delay on Conversational Behavior on Echo-Free Telephone Circuits. Bell Sys. Tech. J., 50, pp.115–34. [13] Perkins C., Hodson O., & V. Hardman, 1998. A Survey of Packet Loss Recovery Techniques for Streaming Audio. IEEE Network, 12(5), pp. 40–48. [14] Číž, P. et al., 2012. VoIP Intrusion Detection System with Snort. s.l.:Slovak University of Technology, Elmar. [15] Practical automated detection of stealthy portscans ’ S. Staniford and J. A. Hoagland and J. M. McAlerney. Journal of Computer Security. Volume 10. Number 1/2. 2002. [16] Al-Naamany, H., Bourdoucen & Al-Menthari, W., 2008. Modeling and Simulation of Quality. Journal of Computing and Information Technology – CIT, 16(2), pp. 131–142. [17] Pan, Y., Chung, J. & Zhang, Z., 2012. ENSC 427 Communication Networks Analysis of Performance of VoIP Over various scenarios: OPNET 14.0. SFU Spring 2012, pp. 3-29.


