Virtual Private Networks
留学生计算机论文代写 Model exploration demonstrated that utilizing a VPN to lead database transactions adds an extra 446% deferral to the inquiry.
Abstract
Virtual Private Networks (VPNs) are a vital piece of ensuring organization correspondences from unapproved review, replication or control. With the goal representatives should remotely direct business in a successful and secure way from a limb area or while voyaging, Virtual Private Networks can be seen as an outright need.
Beginning with a certain set of system correspondence necessities, our venture’s speculation was that the most suitable VPN usage for Cheap Flats (an invented organization we made) would be an Ipsec customer VPN. Included in the report are essential definitions, usage and tests for three separate sorts of VPNs that were utilized to affirm this speculation: 留学生计算机论文代写
The test results from the above VPN executions have been distributed and examinations were made between the diverse sorts of VPNs in regards to the time taken to apply arrange gadget/end-client setups, costs brought about in getting extra gear/programming to actualize the VPN (if any), effect on end-clients, adaptability and ultimately, the general usefulness of the VPN arrangement as it identifies with the normal business operations. Taking after the testing stage, an examination of the benefits and disadvantages of each of the VPN usage was drafted. After which, a last suggestion was displayed in regards to the VPN arrangement that best fit the needs of the theoretical organization portrayed in the paper.
译文:
摘要 留学生计算机论文代写
虚拟专用网络 (VPN) 是确保组织通信不受未经批准的审查、复制或控制的重要组成部分。目标代表应该以成功和安全的方式从边缘区域或在航行中远程指导业务,虚拟专用网络可以被视为一种直接需求。
从一组特定的系统通信必需品开始,我们的企业推测,最适合廉价公寓(我们发明的组织)使用的 VPN 将是 Ipsec 客户 VPN。报告中包含了三种不同类型的 VPN 的基本定义、使用和测试,这些 VPN 被用来证实这一推测:
上述 VPN 执行的测试结果已经分发,并在不同类型的 VPN 之间进行了有关应用安排小工具/终端客户端设置所需的时间、获得额外设备/编程以实现 VPN 所带来的成本的检查(如果有)、对终端客户的影响、适应性以及最终的 VPN 安排的一般用途,因为它与正常业务运营相一致。在测试阶段之后,起草了对每种 VPN 使用的优缺点的检查。之后,显示了关于最适合论文中描述的理论组织需求的 VPN 安排的最后建议。
Introduction
The expenses to a business and its notoriety from stolen, controlled or debased information can be destroying. Prior to the appearance of the Internet, delicate business reports were shielded by either putting them in a safe area (bank vault, bolted documenting bureau, and so forth or by utilizing some basic substitution figures. These figures supplanted the characters in the first message with different images, digits or letters. This implied that the encoded message could just be decoded by somebody who had information of the make-up of the substitution figure. Unless, obviously, an out message without having genuine learning of the substitution figure. 留学生计算机论文代写
This methodology of searching for approaches to scramble information in the most secure way conceivable while staying one stage in front of those looking to decode that same information has proceeded for quite a long time. Notwithstanding, two real contrasts have happened in the field of cryptography and secure correspondences since the coming of processing and the Internet: 1) Access to data (even of the most private kind) has never been less demanding to acquire since a significant part of the data is no more physically secured and 2) Even the absolute most secure routines for encryption cannot withstand the computational invasion of machines committed to running trillions of figuring for every second.
To avert unapproved access to touchy business materials as they cross the Internet, the idea of Virtual Private Networks (VPNs) was imagined. Richard Deal, in his book, “The Complete Cisco VPN in its most straightforward structure “as an association, VPN that are not so much coordinated joined.” State that a good VPN on to arrangement will ordinarily address the majority of the beneath focus (Hwang & Li, 2010)
译文:
介绍 留学生计算机论文代写
被盗、受控制或贬低的信息给企业带来的费用及其臭名昭著可能是毁灭性的。在 Internet 出现之前,通过将敏感的业务报告放在安全区域(银行金库、用螺栓固定的文件局等)或使用一些基本替代数字来屏蔽精细的业务报告。这些数字用以下字符代替了第一条消息中的字符不同的图像,数字或字母。这意味着编码的消息只能由知道替代图形组成信息的人解码。除非,显然,没有真正了解替代图形的输出消息。
这种以最安全的方式搜索加扰信息的方法,同时在那些希望解码相同信息的人面前保持一个阶段,这种方法已经进行了很长时间。尽管如此,自从处理和互联网出现以来,密码学和安全通信领域发生了两个真正的对比:1) 获取数据(即使是最私密的类型)的要求从未如此低数据在物理上不再受到保护,并且 2) 即使是绝对最安全的加密例程也无法承受致力于每秒运行数万亿次计算的机器的计算入侵。
为了避免在敏感的商业资料通过互联网时未经批准的访问,虚拟专用网络 (VPN) 的想法应运而生。理查德·迪尔 (Richard Deal) 在他的书《最简单结构中的完整 Cisco VPN》中,“作为一个协会,没有那么多协调的 VPN 被加入。” 指出一个好的 VPN 安排通常会解决大多数问题(黄 & 李, 2010)
1.1 Project Background
This task is focused around an anecdotal land organization (Cheap Flats) that began with one primary office and a couple of offers delegates. A specimen (censured) topology of the organization’s current system can be found underneath the Methodology segment 1.4. After gigantic development in their essential market, the organization was looking to grow its operations and open a remote extension office in a city a few hundred miles far from their primary office. The extension office will be extensively more modest than the primary office, comprising just a couple of land operators and an office director.
译文:
1.1 项目背景
这项任务的重点是一个轶事土地组织(廉价公寓),该组织从一个主要办公室和几个要约代表开始。 可以在方法论部分 1.4 下找到组织当前系统的样本(受谴责)拓扑。 在其重要市场取得巨大发展后,该组织希望扩大其业务,并在距其主要办事处数百英里的城市开设远程分机办事处。 扩展办公室将比主要办公室更为朴素,仅由几名土地经营者和一名办公室主任组成。
1.2 objectives
The principle objective for this task was to support Cheap Flats with securing secure information interchanges between their new remote extension office and the fundamental office. Since a point-to-point serial association has been esteemed excessively excessive, the organization needed to execute a VPN arrangement utilizing their current Internet associations comprising of a fast fiber association at the principle office and an ADSL association at the remote extension.
The following are a percentage of the essentials that were detailed by the organization president:
- Workers at the remote limb should have the capacity to interface safely to the fundamental office LAN utilizing their Pcs. 留学生计算机论文代写
- The remote limb office workers need access to the accompanying administrations on the principle office LAN: customer database put away on web server, email put away on nearby server, legacy Excel program for making new condo rental postings and finally the organization Intranet containing vital guidelines/regulations relating to new postings.
- The VPN should be executed in the most practical way conceivable since the new limb is planned to be up and running before the end of 2013 (Hwang & Li, 2010).
- Since in the not so distant future has been particularly beneficial so far, the buy of new systems administration supplies up to $10,000 has been endorsed if essential.
译文:
1.2 目标
此任务的主要目标是支持廉价公寓确保其新的远程分机办公室和基础办公室之间的安全信息交换。由于点对点串行关联被过度重视,该组织需要利用他们当前的 Internet 关联来执行 VPN 安排,其中包括主局的快速光纤关联和远程分机的 ADSL 关联。
以下是组织主席详述的基本要素的百分比:
- 远程工作人员应该有能力使用他们的个人电脑安全地连接到基本的办公室 LAN。
- 远程办公室工作人员需要访问主要办公室 LAN 上的随附管理:客户数据库存放在 Web 服务器上,电子邮件存放在附近服务器上,用于制作新公寓租赁发布的旧 Excel 程序,最后是包含重要指导方针的组织内联网/有关新职位的规定。
- 由于新分支计划在 2013 年底之前启动并运行,VPN 应该以最实用的方式执行(Hwang & Li,2010)。
- 由于在不久的将来特别有益,因此如果必要,购买高达 10,000 美元的新系统管理用品已得到认可。
1.3Project Goals
Our task objectives were to arrange and test three separate sorts of VPNs to affirm that the VPN best suited to meet the majority of the essentials laid out by the organization president under the goals area above is an Ipsec Client VPN.
Keeping in mind the end goal to do this, we actualized and tried the accompanying sorts of VPNs:
1) site-to-site: Tunnel mode association between VPN doors. The methodology of encoding and exchanging information between systems is transparent to end-clients.
2) IPsec customer: Network Layer VPN for both system to-system and remote-access organizations. End-clients will need to run either Cisco or Open Source VPN programming on their Pcs. 留学生计算机论文代写
3) Clientless -accessssl: VPN technology “remote that provides Presentation Layer
Encryption administrations for Applications through neighborhood redirection on the customer.” interchanges are built utilizing a program instead of particular programming introduced on the end-client’s gadget.
译文:
1.3项目目标
我们的任务目标是安排和测试三种不同的 VPN,以确认最适合满足组织总裁在上述目标区域下列出的大多数基本要素的 VPN 是 Ipsec 客户端 VPN。
牢记这样做的最终目标,我们实现并尝试了随附的各种 VPN:
1) 站点到站点:VPN 门之间的隧道模式关联。 在系统之间编码和交换信息的方法对终端客户是透明的。
2) IPsec 客户:系统到系统和远程访问组织的网络层 VPN。 最终客户需要在他们的 PC 上运行 Cisco 或开源 VPN 编程。
3)Clientless -accessssl:VPN技术“远程提供表示层
通过客户的邻居重定向对应用程序进行加密管理。”交换是利用程序而不是在终端客户端的小工具上引入的特定编程来构建的。
1.4Methodology
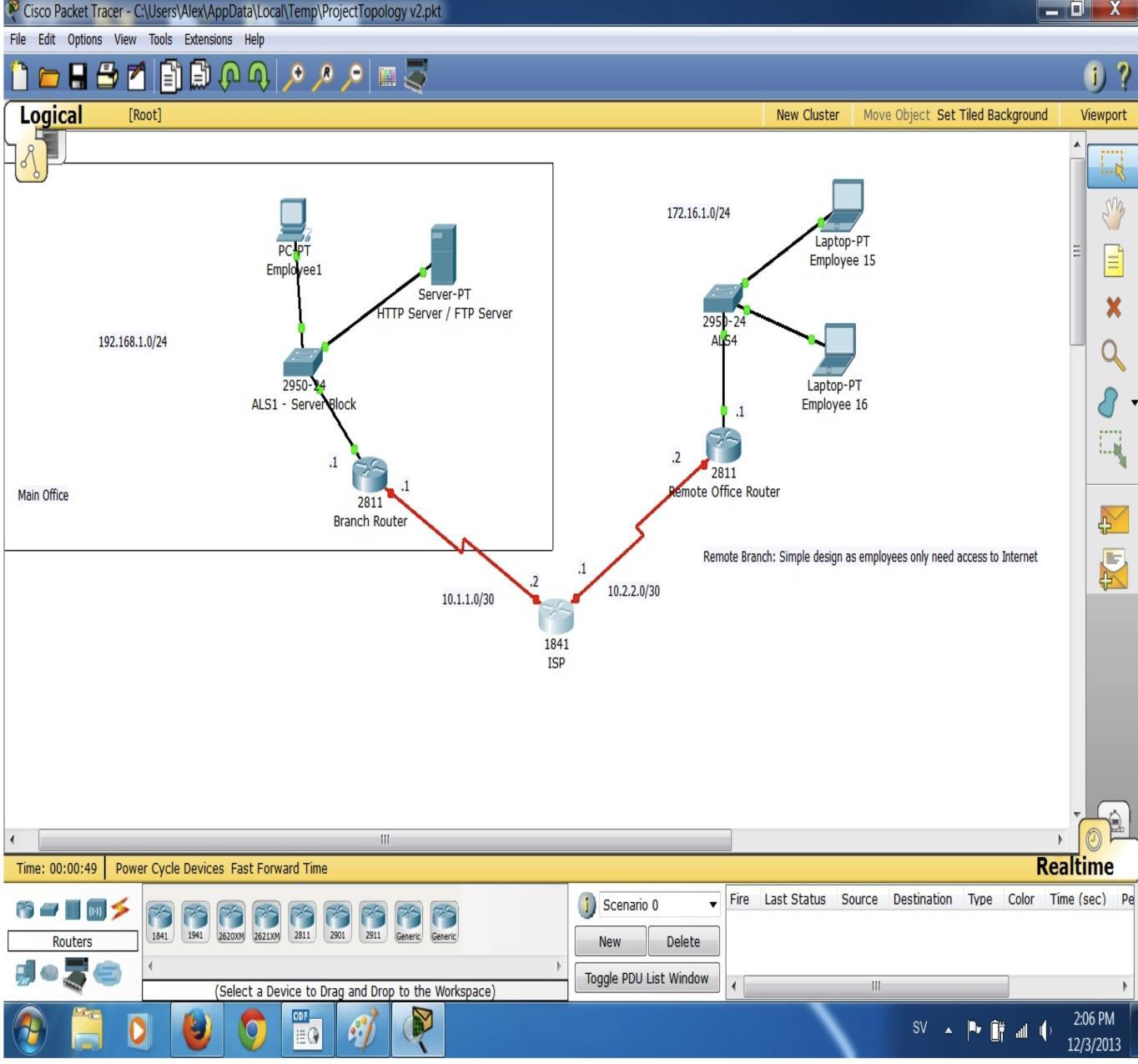
The systems used to test the accomplishment of the undertaking were executed in either the Cisco research facility at the University or in Gns3 utilizing a copy of Cheap Flats existing Network Topology. To start with, the example system was assembled and tried without any encryption at all to guarantee fruitful correspondences between the fundamental office and remote extension. At that point the diverse sorts of VPNs were executed and the results recorded. A deplored perspective of the topology made utilizing Cisco’s Packet Tracer project is given underneath.
译文:
1.4 方法论
用于测试任务完成情况的系统是在大学的 Cisco 研究设施中执行的,或者在 Gns3 中使用廉价公寓现有网络拓扑的副本执行的。 首先,示例系统在完全没有任何加密的情况下组装和试用,以保证基本办公室和远程分机之间富有成效的通信。 那时,执行了各种 VPN 并记录了结果。 下面给出了利用 Cisco 的 Packet Tracer 项目制作的拓扑的令人遗憾的观点。
Figure 1.1 –packet Tracer Topology: representation of censured system topology
Literature Review
2 Basics of VPN
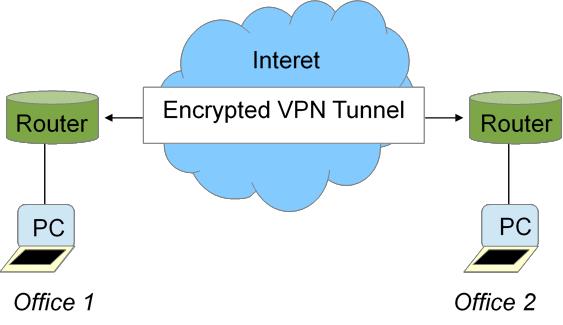
2.1Site-to-site VPN
A Virtual Private Network (VPN) is a correspondences environment that uses virtual associations directed through the Internet by encoding the activity. One of the essential sorts of VPN systems is a site-to-site VPN. It alludes to executions in which the system of one area is associated with the system of an alternate area through a VPN. Edge Relay, ATM, and MPLS VPNs are cases of site-to-site VPNs. One of the gimmicks of the site-to-site VPN is that has don’t have VPN customer programming. Rather, they simply send and get ordinary TCP/IP activity through a VPN entryway. 留学生计算机论文代写
The VPN door is in charge of the encryption and epitome of the outbound movement. That implies that there is a VPN burrow through which correspondence can be secured between companions over the Internet. Upon receipt, the associate VPN door strips the headers, unscrambles the substance, and transfers the parcel around the target have inside its private system. Essentially the site-to-site VPN amplifies the organization’s system making correspondence less demanding. A decent sample here could be an organization with extensions in a few remote areas.
译文:
文献评论 留学生计算机论文代写
2 VPN 基础
2.1站点到站点VPN
虚拟专用网络 (VPN) 是一种通信环境,它通过对活动进行编码来使用通过 Internet 定向的虚拟关联。 VPN 系统的一种基本类型是站点到站点 VPN。它暗示了一个区域的系统通过 VPN 与另一个区域的系统相关联的执行。 Edge Relay、ATM 和 MPLS VPN 是站点到站点 VPN 的例子。站点到站点 VPN 的噱头之一是没有 VPN 客户编程。相反,它们只是通过 VPN 入口发送和获取普通的 TCP/IP 活动。
VPN 门负责出站移动的加密和缩影。这意味着有一个 VPN 洞穴,通过它可以保护同伴之间通过 Internet 的通信。收到后,关联的 VPN 门会剥离标题,解密内容,并将包裹转移到目标在其私有系统中的周围。从本质上讲,站点到站点 VPN 放大了组织的系统,从而降低了通信要求。一个体面的样本可能是在几个偏远地区进行扩展的组织。
Figure 2.1 –site-to-site VPN Tunnel: basic graphical delineation of a site-to-site VPN
2.2Site-to-site GRE Tunnel
Generic Routing Encapsulation is a tunneling protocol developed by Cisco Systems. The main function of this protocol is to encapsulate a variety of network layer protocols within a virtual point-to-point link over an IP internetwork. The advantage of GRE Tunnel is that it supports transport of multicast and broadcast traffic unlike the IPSec which supports only unicast traffic over the tunnel link.
译文:
2.2Site-to-Site GRE隧道
通用路由封装是 Cisco Systems 开发的隧道协议。 该协议的主要功能是在 IP 互联网络上的虚拟点对点链路中封装各种网络层协议。 GRE 隧道的优势在于它支持多播和广播流量的传输,这与 IPSec 不同,IPSec 仅支持隧道链路上的单播流量。
2.3IPSec Remote Access VPN
For remote access VPN integration with full joining into the LAN it is important to utilize an Ipsec VPN association between a VPN Gateway and a remote customer. Rather than SSL, which works at the application layer and is commonly constrained to web applications or a web entrance, Ipsec is a connectionless convention that works at Layer-3. With Ipsec VPN it is conceivable to give the remote client full or custom access to the LAN with a client encounter as though the remote client were physically associated inside the LAN. Additionally, little doubt remains to gadgets inside the LAN that the remote client was physically show. At the end of the day, full system expansion can be attained. An Ipsec VPN organization is especially essential when the remote client needs to get to applications that can’t be overseen through a web entrance, for example, an ERP or legacy programming. 留学生计算机论文代写
In spite of the fact that it offers more potential outcomes in the system, Ipsec is frequently contrasted with SSL/TLS as being more muddled with expanded managerial overhead. Notwithstanding this downside, an alternate disadvantage to the Ipsec Remote Access VPN. Methodology is that the VPN customer programming must be introduced machine with managerial benefits which can prevent versatility in huge scale organizations. An alternate test with Ipsec VPNs can be exploring through firewalls and NAT gadgets that are arranged between the customer and the portal. (Matei 2012) Thankfully there are devices accessible that can help resolve these difficulties, for example, NAT Traversal. Cisco’s execution of this it alternative is the one is called decided to execute for this venture.
译文:
2.3IPSEC远程访问VPN
对于完全加入 LAN 的远程访问 VPN 集成,利用 VPN 网关和远程客户之间的 Ipsec VPN 关联非常重要。与 SSL 不同,SSL 在应用层工作并且通常被限制在 Web 应用程序或 Web 入口,Ipsec 是一种在第 3 层工作的无连接约定。使用 Ipsec VPN 可以想象,在遇到客户端时,远程客户端可以完全或自定义访问 LAN,就好像远程客户端在 LAN 内部物理关联一样。此外,远程客户端物理展示的 LAN 内的小工具几乎没有任何疑问。最终,可以实现完整的系统扩展。当远程客户端需要访问无法通过 Web 入口进行监控的应用程序(例如,ERP 或传统编程)时,Ipsec VPN 组织尤其重要。
尽管事实上它在系统中提供了更多潜在的结果,但 Ipsec 经常与 SSL/TLS 形成对比,因为它更容易被扩展的管理开销所困扰。尽管有这个缺点,但 Ipsec 远程访问 VPN 的另一个缺点。方法论是,必须将 VPN 客户编程引入具有管理优势的机器,这可以防止大型组织中的多功能性。使用 Ipsec VPN 的替代测试可以通过在客户和门户之间安排的防火墙和 NAT 小工具进行探索。 (Matei 2012) 值得庆幸的是,有一些可访问的设备可以帮助解决这些困难,例如 NAT Traversal。思科的这个替代方案被称为决定为这个企业执行。
2.4IPSec VPN
IPSec is an IETF standard that acts as a modular framework of open standards that define how a VPN connection is implemented. The three main security solutions IPSec offers are data integrity, data authentication, and data confidentiality.
Data integrity is accomplished through the use of HMAC, a standard that uses a hash algorithm to create a hash value that is sent along with the packet. Upon receipt, the hash algorithm is run again and compared to the received hash value. The hash values must be identical for the packet to be accepted. The two hash algorithms available to use in IPSec are MD5 and SHA-1. 留学生计算机论文代写
Data authentication is achieved through pre-shared keys, RSA signatures (digital signatures), or RSA encrypted nonces.
Data confidentiality is attained by encrypting the data. Common encryption algorithms that are available in IPSec are DES, 3DES, AES, and SEAL
译文:
2.4IPSEC VPN
IPSec 是一种 IETF 标准,它充当定义 VPN 连接如何实现的开放标准的模块化框架。 IPSec 提供的三个主要安全解决方案是数据完整性、数据验证和数据机密性。
数据完整性是通过使用 HMAC 来实现的,HMAC 是一种使用哈希算法创建与数据包一起发送的哈希值的标准。 收到后,再次运行散列算法并与接收到的散列值进行比较。 要接受的数据包,哈希值必须相同。 可用于 IPSec 的两种散列算法是 MD5 和 SHA-1。
数据身份验证是通过预共享密钥、RSA 签名(数字签名)或 RSA 加密随机数实现的。
数据机密性是通过对数据进行加密来实现的。 IPSec 中可用的常见加密算法有 DES、3DES、AES 和 SEAL
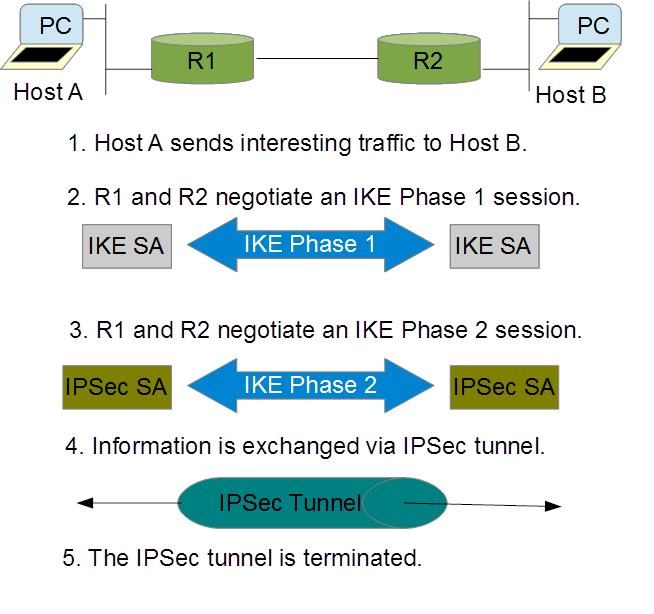
Triggering the VPN Connection
There are two ways that an IPSec VPN connection can be set into motion. In a site-
to-site connection, “interesting traffic” is ide traffic that is permitted by the ACL triggers the IKE process. In a remote client connection, the user initiates the connection manually by clicking on the connection profile in the software client.

Internet Key Exchange (IKE)
IKE is used by IPSec to negotiate and establish multiple Security Associations (SA). The implementation is divided into two phases. 留学生计算机论文代写
IKE Phase 1
The first SA is created during IKE Phase 1 and is essentially a control channel. The purpose of the first phase is to establish a secure and authenticated channel that will allow secure Phase 2 negotiations to take place. [8] It also authenticates the peers.
It works at 2 modes:
译文:
触发 VPN 连接 留学生计算机论文代写
有两种方法可以启动 IPSec VPN 连接。 在一个站点——
到站点连接,“有趣的流量”是 ACL 允许触发 IKE 进程的 ide 流量。 在远程客户端连接中,用户通过单击软件客户端中的连接配置文件手动启动连接。
互联网密钥交换 (IKE)
IPSec 使用 IKE 来协商和建立多个安全关联 (SA)。 实施分为两个阶段。
IKE 阶段 1
第一个 SA 是在 IKE 阶段 1 期间创建的,本质上是一个控制通道。 第一阶段的目的是建立一个安全且经过身份验证的通道,允许进行安全的第二阶段协商。 [8] 它还验证对等方。
它在 2 种模式下工作:
Figure -IPSec negotiation process
2.5 Secure Sockets Layer (SSL)
The SSL convention was initially created by Netscape as an approach to give secure transmission of data between a server a done to a limited extent to attempt and reinforce the capacity of e-trade organizations to furnish their online customers with a protected and solid experience. The SSL convention is executed at the Transport Layer and upwards in the seven layer Open Systems Interconnection (OSI) system model. As opposed to Ipsec, the layer 3 (source and goal IP address) data is not encoded. The whole secure correspondences transform in the middle of customer and server is very perplexing however can be broken down into a nine-stage process. This handshake methodology is very comparative when utilizing TLS.
Ibm’s web sphere online entryway, which is the wellspring of the realistic handshake methodology representation above, additionally gives a short rundown of the SSL handshake technique as takes after: 留学生计算机论文代写
1) The” ssl or TLS customer sends a “customer hi” message that rundowns cryptographic data, for example, the SSL or TLS rendition and, in the customer’s request of inclination, the Cipher suites underpinned by the customer. The message additionally contains an irregular byte string that is utilized as a part of ensuing calculations. The convention considers the “customer hi” to incorporate the information layering techniques underpinned by the customer.
2) The SSL or TLS server reacts with a “server hi” message that contains the Ciphersuite picked by the server from the rundown gave by the customer, the session ID, and an alternate arbitrary byte string. The server additionally sends its advanced endorsement. On the off chance that the server obliges an advanced authentication for customer verification, the server sends a “customer declaration ask for” that incorporates a rundown of the sorts of authentications underpinned and the Distinguished Names of adequate Certification Authorities (Cas).
译文:
2.5 安全套接字层(SSL)
SSL 约定最初由 Netscape 创建,作为一种在服务器之间安全传输数据的方法,目的是在有限的范围内尝试和加强电子贸易组织为其在线客户提供受保护和可靠体验的能力。 SSL 约定在传输层执行,并在七层开放系统互连 (OSI) 系统模型中向上执行。与 Ipsec 不同,第 3 层(源和目标 IP 地址)数据未编码。在客户和服务器中间的整个安全通信转换非常令人困惑,但可以分解为九个阶段的过程。这种握手方法在使用 TLS 时非常具有比较性。
IBM 的 Web Sphere 在线入口是上述现实握手方法的源泉,另外还简要介绍了 SSL 握手技术,如下所示:
1) ssl 或 TLS 客户发送一个“customer hi”消息,该消息会破坏加密数据,例如 SSL 或 TLS 格式,以及在客户的要求中,客户支持的密码套件。该消息还包含一个不规则字节串,用作后续计算的一部分。约定认为“客户好”包含了由客户支持的信息分层技术。
2) SSL 或 TLS 服务器对“服务器嗨”消息做出反应,该消息包含服务器从客户提供的纲要中选择的密码套件、会话 ID 和备用的任意字节字符串。服务器另外发送其高级背书。如果服务器有义务对客户验证进行高级身份验证,服务器会发送“客户声明请求”,其中包含支持的各种身份验证和适当证书颁发机构 (Cas) 的专有名称的概要。
3) The SSL or TLS customer checks the server’s computerized authentication.
4) The SSL or TLS customer sends the irregular byte string that empowers both the customer and the server to figure the mystery key to be utilized for encoding consequent message information. The irregular byte string itself is encoded with the server’s open key.
5) If the SSL or TLS server sent a “customer declaration ask for”, the customer sends an irregular byte string scrambled with the customer’s private key, together with the customer’s advanced authentication, or a “no computerized testament caution”. This alarm is just a cautioning, however with a few executions the handshake comes up short if customer validation is required. 留学生计算机论文代写
6) The SSL or TLS server confirms the customer’s testament.
7) The SSL or TLS customer sends the server a “completed” message, which is scrambled with the mystery key, demonstrating that the customer piece of the handshake is finished.
8) The SSL or TLS server sends the customer a “completed” message, which is scrambled with the mystery key, showing that the server piece of the handshake is finished.
9) For the length of time of the SSL or TLS session, the server and customer can now trade messages that are symmetrically encoded with the imparted mystery key.”
译文:
3) SSL 或 TLS 客户检查服务器的计算机化身份验证。
4) SSL 或 TLS 客户发送不规则字节串,使客户和服务器都能够计算出用于编码后续消息信息的神秘密钥。不规则字节串本身是用服务器的公开密钥编码的。
5) 如果 SSL 或 TLS 服务器发送“客户声明请求”,则客户发送一个不规则字节串,用客户的私钥加扰,连同客户的高级身份验证,或“无计算机化遗嘱警告”。这个警报只是一个警告,但是如果需要客户验证,几次执行握手会很短。
6) SSL 或 TLS 服务器确认客户的遗嘱。
7) SSL 或 TLS 客户向服务器发送一条“完成”消息,该消息与神秘密钥一起加扰,表明客户部分的握手已完成。
8) SSL 或 TLS 服务器向客户发送“完成”消息,该消息与神秘密钥一起加扰,表明握手的服务器部分已完成。
9) 在 SSL 或 TLS 会话的时间长度内,服务器和客户现在可以交换使用传递的神秘密钥对称编码的消息。”
Encapsulating Security Payload
Encapsulating Security Payload (ESP)is intended to give a few security administrations, including information secrecy, respectability, and beginning validation among other important assurances. The measure of dependence on ESP relies on either shaft or transport mode of operation. On the off chance that information is constantly sent in the supposed ‘passage mode’ then “Ipsec makes another IP parcel that contains the Ipsec segment and embodies the first unsecured bundle”. In the event that the information is continuously sent in transport mode then there is no internal header. This implies that the conventions give security by making segments of the Ipsec header in the meantime the source produces other IP header data. 留学生计算机论文代写
Every ESP headers is embedded after the IP header. In the event that a bundle is ensured in transport mode the ESP header basically takes after the first header. The parcel is stretched from the IP header, TCP and information to another bundle with the first IP header, emulated by the ESP header, the TCP, Data, ESP Trailer and ESP approval. On the off chance that you read this, please email the writer of this oddity at his email recorded on the last page. While in transport mode, the ESP additionally guarantees that the TCP, Data and ESP trailer are all encoded. Just the first IP header, ESP header and ESP approval are not encoded. The bundle is additionally confirmed with the exception of the first IP header and ESP approval. ESP is recognized by an estimation of 50 in the IP header
译文:
封装安全负载 留学生计算机论文代写
封装安全有效负载 (ESP) 旨在提供一些安全管理,包括信息保密、可敬性和开始验证以及其他重要保证。对 ESP 的依赖程度取决于竖井或运输操作模式。如果信息以假定的“通道模式”不断发送,则“Ipsec 制作另一个包含 Ipsec 段并包含第一个不安全捆绑包的 IP 包”。如果信息以传输模式连续发送,则没有内部报头。这意味着约定通过在源生成其他 IP 标头数据的同时制作 Ipsec 标头的段来提供安全性。
每个 ESP 标头都嵌入在 IP 标头之后。如果在传输模式下确保捆绑包,则 ESP 标头基本上位于第一个标头之后。包裹从 IP 标头、TCP 和信息延伸到具有第一个 IP 标头的另一个包,由 ESP 标头、TCP、数据、ESP 拖车和 ESP 批准模拟。万一你读到了这篇文章,请通过最后一页上记录的电子邮件给这个奇怪的作者发电子邮件。在传输模式下,ESP 额外保证 TCP、数据和 ESP 尾部都被编码。只是第一个 IP 标头、ESP 标头和 ESP 批准未编码。除了第一个 IP 标头和 ESP 批准外,还对捆绑进行了确认。 ESP 通过 IP 头中估计为 50 来识别
Generally, that a bundle is secured under shaft mode the parcel is additionally stretched from the IP header, TCP and information.
This new parcel contains a totally new IP header emulated by the ESP header, and the first IP header, TCP, Data, ESP Trailer and ESP Authorization. Of the data in the bundle all is encoded with the exception of the new IP header, ESP header and the ESP auth. The whole parcel is additionally confirmed with the exception of the new IP header and the ESP approval. 留学生计算机论文代写
Every ESP header has a 32 bit esteem that is joined with the end address and convention in the former IP header, recognizing the security relationship to be utilized to process the parcel. This 32-bit worth is known as the security parameter record (SPI). This SPI is utilized as a list number. It can be utilized to find the security relationship in the security affiliation database.
译文:
通常,在 SHAFT 模式下保护包裹的包裹额外从 IP 标头、TCP 和信息延伸。
这个新包包含一个由 ESP 标头模拟的全新 IP 标头,以及第一个 IP 标头、TCP、数据、ESP 拖车和 ESP 授权。 除了新的 IP 标头、ESP 标头和 ESP 身份验证外,捆绑包中的所有数据都进行了编码。 除了新的 IP 标头和 ESP 批准外,整个包裹还得到了额外确认。
每个 ESP 标头都有一个 32 位自尊,它与前 IP 标头中的结束地址和约定相结合,识别用于处理包裹的安全关系。 这个 32 位值称为安全参数记录 (SPI)。 该 SPI 用作列表编号。 可用于在安全关联数据库中查找安全关系。
There is additionally a succession number that is haphazardly picked by the goal end of the passage amid the Internet Key Exchange (IKE) arrangement between the two closures of the shaft.
This number “is a novel monotonically expanding number that is embedded into the header by the sender”. Note that the arrangement number is not the same as the security parameter list. The grouping number serves as a hostile to replay gadget. Against replay is a kind of assault where a person who has been watching the transmission of parcels tries to send a comparable bundle to the portal. Ipsec is organized to utilize a 64-bundle hostile to replay window. Ipsec utilizes this window to recognize parcels that could possibly be from a replay assault. 留学生计算机论文代写
The passage at the less than desirable end of the shaft would create the grouping number. This number could theoretically be N. This implies that the passage will acknowledge any parcel with a succession number between N-64 and N. Parcels that touch base with a grouping number less then N-64 and more prominent than N abuse the guideline. These parcels are accepted to originate from an assailant.
译文:
此外,在杆身的两个封闭件之间的 Internet 密钥交换 (IKE) 安排中,还有一个由通道的目标端偶然选择的继任号。
这个数字“是一个新的单调扩展的数字,由发送者嵌入到报头中”。请注意,排列编号与安全参数列表不同。分组号用作重播小工具的敌意。反对重播是一种攻击,在这种情况下,一直在观察包裹传输的人试图将类似的包裹发送到门户。 Ipsec 被组织成利用 64 包敌对重播窗口。 Ipsec 利用此窗口识别可能来自重放攻击的包裹。
轴的不太理想端的通道将产生分组数。这个数字理论上可以是 N。这意味着该段落将确认任何继承编号在 N-64 和 N 之间的包裹。与分组编号小于 N-64 且比 N 更突出的包裹接触基地滥用了该准则。这些包裹被接受为来自攻击者。
Authentication Header
Verification Header (AH) does not give information secrecy. It does empower connectionless trustworthiness, information confirmation and discretionary replay security. Since it doesn’t give information classifiedness it has a much less complex header than ESP. Ok is recognized by the estimation of 51 in the IP header.
Under transport mode the IP bundle is not changed fundamentally. The AH takes after the first IP header of the IP parcel. After the AH, the TCP and information make up whatever is left of the parcel. Under passage mode the bundle is not modified whatsoever. Rather, another IP header is added to the parcel emulated by the AH and whatever remains of the bundle
译文:
身份验证标头
验证头 (AH) 不提供信息保密。 它确实增强了无连接的可信度、信息确认和任意重放安全性。 由于它不提供信息分类,因此它的标头比 ESP 复杂得多。 Ok是通过IP头中51的估计来识别的。
在传输模式下,IP 捆绑没有从根本上改变。 AH 位于 IP 包的第一个 IP 标头之后。 在 AH 之后,TCP 和信息构成了包裹的剩余部分。 在通过模式下,捆绑包不会被修改。 相反,另一个 IP 标头被添加到由 AH 模拟的包以及包的任何剩余部分
VPN Summary
VPNs need four key components from the Ipsec Protocol security conventions, key trade instruments, and calculations needed for encryption and secure key trade, and SA definitions and upkeep. Ipsec however fulfills this at layer 3. Due to the local security in Ipsec VPNs, this innovation has turned into the commanding convention utilized as a part of today’s venture, administration suppliers, and government systems.
Ipsec was created while the up and coming era of IP conventions, Ipv6, was being produced.
This implied that Ipsec would be locally underpinned in Ipv6. However when appropriation of Ipv6 was moderate, it was chosen to make Ipsec retrograde perfect with Ipv4 to give security to the Ipv6 parcels. In 2008 product engineer Steinar H. Gunderson, who lives up to expectations for Google, finished a study that found that Ipv6 entrance was still short of what one percent of Internet-empowered has in any nation. This implies that VPN applications can keep on depending upon and use Ipsec for a long time to come (Panko, 2010). Through Ipsec VPNs can fulfill information secrecy, information uprightness, sender non-renouncement and message confirmation. Ipsec’s local cryptography, hashes, and headers convention deliver an extremely secure and stable VPN application. 留学生计算机论文代写
Utilizing a VPN obliges no lasting connections between end hubs that oblige a month to month charge and contract arrangement. VPNs don’t oblige any particular supplies. This is a colossal point of interest over rented lines or edge transfer systems. In short, a VPN is a shoddy wellspring of “burrowing, encryption, verification and access control innovations and administrations used to convey movement over the web, an oversaw IP system, or a supplier’s spine” (Rohde et al,. 2010)
译文:
VPN总结
VPN 需要来自 Ipsec 协议安全公约的四个关键组件、关键交易工具以及加密和安全密钥交易所需的计算,以及 SA 定义和维护。然而,Ipsec 在第 3 层实现了这一点。由于 Ipsec VPN 的本地安全性,这一创新已转变为命令惯例,用作当今风险投资、管理供应商和政府系统的一部分。
Ipsec 是在 IP 约定的新兴时代 Ipv6 正在产生的同时创建的。
这意味着 Ipsec 将在 Ipv6 中得到本地支持。然而,当Ipv6的占用量适中时,选择使Ipsec逆行与Ipv4完美结合,以确保Ipv6包的安全。 2008 年,对 Google 不负众望的产品工程师 Steinar H. Gunderson 完成了一项研究,该研究发现 IPv6 入口仍然比任何国家的 1% 的互联网赋能者都少。这意味着 VPN 应用程序可以在很长一段时间内继续依赖和使用 Ipsec(Panko,2010)。通过 Ipsec VPN 可以实现信息保密、信息正直、发送方不放弃和消息确认。 Ipsec 的本地加密、散列和标头约定提供了极其安全和稳定的 VPN 应用程序。
使用 VPN 不需要终端集线器之间的持久连接,而后者需要按月收费和合同安排。 VPN 不要求任何特定的供应品。这是对租用线路或边缘传输系统的一个巨大兴趣点。简而言之,VPN 是“挖掘、加密、验证和访问控制创新和管理的劣质源泉,用于通过网络传达运动、监督 IP 系统或供应商的脊椎”(Rohde 等人,2010 年)
Test Model Development
OPNET IT Guru Software permits clients to test the execution of speculative systems. The product utilizes genuine information to foresee the execution of models that are made. The scholarly form of OPNET IT Guru programming was utilized as a part of model testing for this paper. The center of model testing was to explicitly figure out what degree, if any, a VPN system would affect a current corporate system. The model was intended to reflect, as almost as could be allowed, a genuine business system.
Model improvement took after the by and large acknowledged adjust approach to position firewalls, switches, servers and Lans. The model was intended to reproduce an organization with three corporate work places. Central station would be placed in the condition of Sydney, with two limb business locales in the southern piece of Queensland and Queensland. The Queensland office servers were appointed information reinforcement and would reflect Headquarters’ servers (Rohde et al,. 2010). 留学生计算机论文代写
The preconfigured hubs that spoke to the Ipcloud, firewalls, switches, switches and Lans where utilized as a part of the model.
The switches utilized were the ethernet4_slip8_gtwy and the firewalls were the ethernet2slip8_firewall. The Internet would be spoken to by the preconfigured ip32_cloud, and the switches would be the ethernet16_switch. The base camp framework comprised of a 100 part LAN, an E-mail, FTP, and database server.
A primary Ds1 line originated from the cloud into the first central command firewall. The Ds1 line then entered the central command switches which sent movement to either the LAN Switch, or the firewalls for email, FTP, and database servers. The LAN switch was served by a 100baset line. The firewalls were all served by a Ds1 line. The LAN switch served the LAN all on 100baset line. The server firewalls were specifically joined with the individual servers by means of a Ds1 line.
译文:
测试模型开发
OPNET IT Guru Software 允许客户测试推测系统的执行。该产品利用真实信息来预测所制造模型的执行情况。 OPNET IT Guru 编程的学术形式被用作本文模型测试的一部分。模型测试的中心是明确地弄清楚 VPN 系统会在多大程度上影响当前的公司系统。该模型旨在尽可能地反映一个真正的商业系统。 .
模型改进是在大体公认的调整方法来定位防火墙、交换机、服务器和 LAN 之后进行的。该模型旨在重现具有三个公司工作场所的组织。中央车站将被置于悉尼的条件下,在昆士兰和昆士兰的南部有两个边缘商业区。昆士兰办公室服务器被指定为信息强化,并将反映总部的服务器(Rohde 等,2010)。
与 Ipcloud、防火墙、交换机、交换机和 LAN 通信的预配置集线器用作模型的一部分。
使用的交换机是 ethernet4_slip8_gtwy,防火墙是 ethernet2slip8_firewall。预先配置的 ip32_cloud 将与 Internet 通话,并且交换机将是 ethernet16_switch。大本营框架由一个 100 部分的 LAN、一个电子邮件、FTP 和数据库服务器组成。
主 Ds1 线路从云开始,进入第一个中央命令防火墙。 Ds1 线路然后进入中央命令交换机,这些交换机将移动发送到 LAN 交换机或电子邮件、FTP 和数据库服务器的防火墙。 LAN 交换机由 100baset 线路提供服务。防火墙都由一条 Ds1 线路提供服务。 LAN 交换机在 100baset 线路上为 LAN 提供服务。服务器防火墙通过 Ds1 线路专门与各个服务器相连。
The Queensland site is home to three 100 part Lans. From the Internet cloud there is a Ds1 line to the Queensland firewall and afterward a Ds1 line to the Queensland switch.
Three switches interface with the switch through 100baset line and the Lans are served by means of 100baset line from the switches. The Queensland information reinforcement site was associated with the IP cloud first through the firewall and afterward switch. Ds1 line ran between the cloud-firewall, and firewall -switch. A Ds1 line joined from the switch to every server firewall. Every server firewall was associated with the server by a Ds1 line. The LAN was overhauled by a 100baset line from the switch which was joined by a 100baset line to the switch. 留学生计算机论文代写
The scholarly form of OPNET IT Guru restricted the testing by constraining the model at 50 hubs. A hub is a switch, firewall, switch or LAN. The product would not run reproductions if more than 50 hubs were put on the model. Two separate profiles were made and afterward connected to the different hubs. The two profiles were Datacenter and Office. The Queensland area LAN had the server farm profile connected to it and the Headquarters and Queensland Lans got the Office profiles. The profiles were situated up as indicated in Table one. Overwhelming or light definitions are given as those by and large acknowledged as normal for a corporate office (Zhou et al,. 2010).
译文:
昆士兰基地是三个 100 部分 Lans 的所在地。从互联网云有一条 Ds1 线路到昆士兰.
三台交换机通过 100baset 线路与交换机接口,局域网通过交换机的 100baset 线路提供服务。昆士兰信息加固站点先通过防火墙与IP云关联,然后切换。 Ds1 线路在云防火墙和防火墙开关之间运行。一条 Ds1 线路从交换机连接到每个服务器防火墙。每个服务器防火墙都通过 Ds1 线路与服务器相关联。 LAN 由来自交换机的 100baset 线路大修,该线路由 100baset 线路连接到交换机。
OPNET IT Guru 的学术形式通过将模型限制在 50 个中心来限制测试。集线器是交换机、防火墙、交换机或 LAN。如果在模型上放置超过 50 个集线器,该产品将无法进行复制。制作了两个单独的配置文件,然后连接到不同的集线器。这两个配置文件是数据中心和办公室。昆士兰地区 LAN 连接了服务器群配置文件,总部和昆士兰 LAN 获得了办公室配置文件。配置文件的位置如表一所示。压倒性或轻量级的定义一般被认为是公司办公室的正常定义(Zhou 等人,2010 年)。
Table 1
| Application | DataCenter | Office | ||
| Database Access | Heavy | Light | ||
| Light | Heavy | |||
| File Transfer | ||||
| Heavy | Heavy | |||
| File Print | ||||
| Light | Heavy | |||
| TeleNet Session | 留学生计算机论文代写 | |||
| Light | Light | |||
| Video Conferencing | ||||
| Light | Light | |||
| Voice Over IP | ||||
| GSM Quality | GSM Quality | |||
| Web Browsing | ||||
| Light | Heavy | |||
Simulation Empirical Results
At the point when the models were finished trying started to focus the effect a VPN has on an organization system. It was accepted that the OPNET Guru IT programming would make a sufficiently shifting environment to recreate genuine results. Starting tests were run for ten minutes. In the wake of examining these results it got to be clear that this run time was deficient to give a precise picture of what was going on the system. Ten minutes was not sufficient time for system movement to develop and give a general normal. 留学生计算机论文代写
Twenty minutes was the longest time the scholastic form of the product would run the recreation. The recreation was restricted by the aggregate sum of occasions that could be performed. An occasion is characterized as an email, document, or database inquiry, being moved over any sort of machine equipment. The two models found the middle value of 250,000 occasions for every second. This brought about a normal aggregate of 47.2 million occasions being figured. System occasion rate was practically identical on both models. Figure 3 demonstrates an illustration of the FTP Download speed from the model with the VPN and without the VPN.
译文:
模拟实证结果
在模型完成时,开始尝试关注 VPN 对组织系统的影响。人们接受 OPNET Guru IT 编程将创造一个充分变化的环境来重新创建真正的结果。启动测试运行了十分钟。在检查这些结果之后,很明显这个运行时间不足以准确描述系统上正在发生的事情。十分钟不足以让系统运动发展并给出一般正常。
二十分钟是该产品的学术形式进行娱乐的最长时间。娱乐活动受到可以进行的总次数的限制。场合的特点是电子邮件、文档或数据库查询,在任何类型的机器设备上移动。这两个模型找到了每秒 250,000 次的中间值。这带来了正常的 4720 万次统计。两种型号的系统发生率几乎相同。图 3 展示了使用 VPN 和不使用 VPN 的模型的 FTP 下载速度。
Figure 3
FTP Download Speed VPN FTP Download Speed
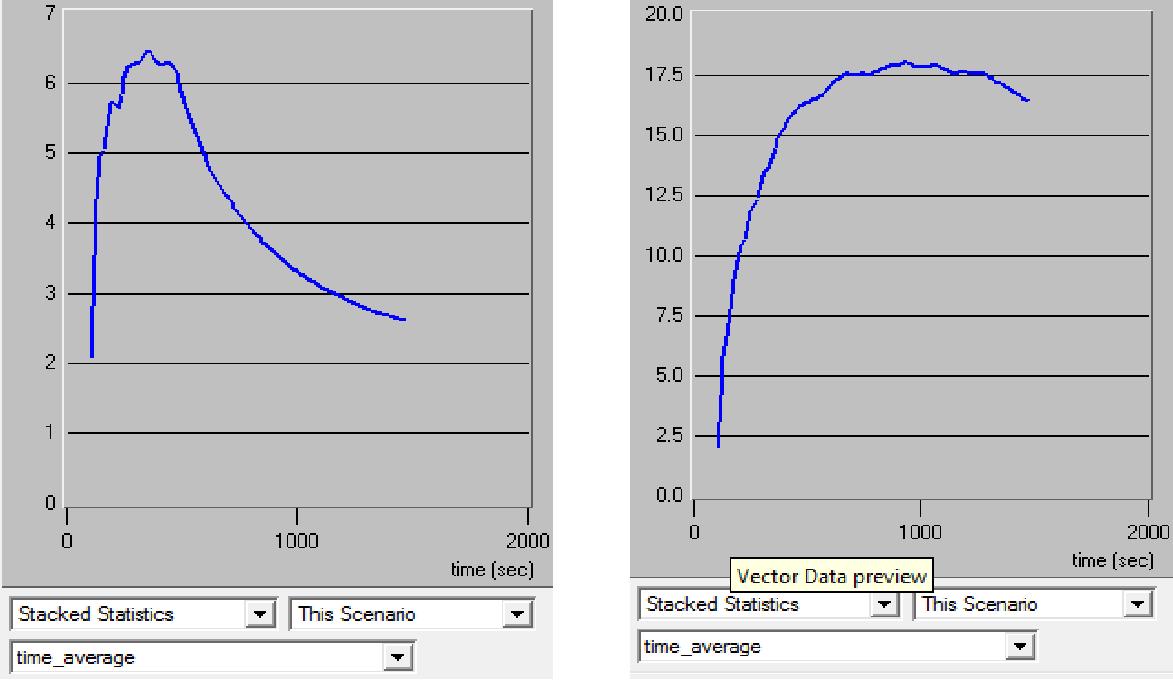
Results were gathered after each one model was run and each one model was run 20 times.
The facts of each one model were introduced in a system created diagram that detailed the action all through the reproduction. This incorporated a normal beginning five moment move in movement as the system was begun. Following five minutes the system action arrived at the midpoint of out as a level of immersion was attained. The product did not give a numeric normal to the different facts; results were gathered by outwardly averaging the presentation.
Reproductions where led to examine the contrasts between the models. Information was gathered on detail, for example, VPN shaft defer and number of bundles sent and got. A two specimen, one tail t-test expecting unequal fluctuations was performed on the information. 留学生计算机论文代写
The examination demonstrated that the normal number of parcels sent in one second for the database request is essentially bigger, 56,925 instead of 54,000, in the model with a VPN than the model without a VPN (t = 2.15, P = 0.021). The VPN overhead, as indicated in table 2, was figured by utilizing the normal database reaction time and separating it by the normal database reaction time for the model with the VPN association. The result was that directing database transactions through a VPN expanded postpone by 446%.
译文:
在每个模型运行后收集结果,每个模型运行 20 次。
每个模型的事实都在系统创建的图表中进行了介绍,该图表详细说明了整个复制过程中的动作。当系统开始时,这包含了一个正常的开始五时刻运动。五分钟后,系统动作达到了浸入的中点。产品没有给出不同事实的数值法线;结果是通过对演示文稿进行外部平均来收集的。
复制品导致检查模型之间的对比。收集了详细信息,例如 VPN 轴延迟以及发送和获取的捆绑包数量。对信息进行了两个样本,一个尾部 t 检验,预期波动不等。
检查表明,在具有 VPN 的模型中,对于数据库请求,一秒钟内发送的正常包裹数量实际上更大,为 56,925,而不是 54,000,与没有 VPN 的模型相比(t = 2.15,P = 0.021)。 VPN 开销,如表 2 所示,是通过利用正常数据库反应时间并将其与具有 VPN 关联的模型的正常数据库反应时间分开来计算的。结果是,通过 VPN 引导数据库事务的延迟时间延长了 446%。
Table 2
| Database Query | Response Time (ms) | |
| VPN Avg | 17.1875 | |
| NO VPN Avg 留学生计算机论文代写 | 3.8525 | |
| T‐Test | 62.11836897 | |
| Average over head added: | 446% | |
Conclusions
Using a VPN brings about a critical increment in system load and time delay. This is, nonetheless, a little cost to pay for the security and protection offered by a virtual private system. VPN is the best and adaptable manifestation of secure correspondence crosswise over long separations. More data transfer capacity is obliged to handle the extra system load. A VPN may oblige a machine equipment overhaul or even extra fittings. In the event that system assets are not created and extended to help; organizations may encounter slower reaction times in email, record conveyance, and database asks.
Model exploration demonstrated that utilizing a VPN to lead database transactions adds an extra 446% deferral to the inquiry. Huge deferral is likewise added to email and FTP transactions. Rented lines and casing hand-off systems were the early extravagant answer for private systems. Their higher costs and more noteworthy equipment necessities lead to the spread of VPN engineering. 留学生计算机论文代写
Advancement of PPTP and L2fp conventions prompted the coordination of VPN innovation. The requirement for expanded security prompted the reconciliation of Ipsec engineering into the current VPN schema. This likewise changed the center of VPN engineering from layer 2 to layer 3. Today clients can remotely get to assets through a safe, modest and advantageous virtual private system.
译文:
结论 留学生计算机论文代写
使用 VPN 会导致系统负载和时间延迟的显着增加。尽管如此,这是为虚拟专用系统提供的安全和保护支付的一点成本。 VPN 是长距离横向安全通信的最佳且适应性强的体现。更多的数据传输容量不得不处理额外的系统负载。 VPN 可能要求机器设备大修甚至额外的配件。如果没有创建和扩展系统资产以提供帮助;组织可能会在电子邮件、记录传输和数据库询问中遇到较慢的反应时间。
模型探索表明,使用 VPN 来引导数据库事务会额外增加 446% 的查询延迟。电子邮件和 FTP 交易同样增加了巨大的延迟。租用线路和套管移交系统是早期对私人系统的奢侈解决方案。它们更高的成本和更值得注意的设备必需品导致 VPN 工程的普及。
PPTP 和 L2fp 约定的进步促进了 VPN 创新的协调。对扩展安全性的要求促使 Ipsec 工程与当前 VPN 模式相协调。这同样将 VPN 工程的中心从第 2 层更改为第 3 层。如今,客户可以通过安全、适度且有利的虚拟专用系统远程访问资产。
References 留学生计算机论文代写
Hwang, K., & Li, D. (2010). Trusted cloud computing with secure resources and data coloring. Internet Computing, IEEE, 14(5), 14-22.
Panko, R. (2010). Corporate Computer and Network Security, 2/e. Pearson Education India.
Wei, D., Lu, Y., Jafari, M., Skare, P., & Rohde, K. (2010, January). An integrated security system of protecting smart grid against cyber attacks. InInnovative Smart Grid Technologies (ISGT), 2010 (pp. 1-7). IEEE.
White, C. (2010). Data communications and computer networks: A business user’s approach. Cengage Learning.
Zhou, M., Zhang, R., Xie, W., Qian, W., & Zhou, A. (2010, November). Security and privacy in cloud computing: A survey. In Semantics Knowledge and Grid (SKG), 2010 Sixth International Conference on (pp. 105-112). IEEE.

更多代写:Mysql代写 留学生金融Final exam代考 留学生金融essay代写 留学生教育学Essay代写 留学生会计论文代写 report报告代写

