COMS3000/7003 – Information Security
Assignment 2 (Due Date: 28 Oct 2020 20:00)
COMS3000/7003作业代写 This assignment give students insight on how firewalls work by playing with network scanning, firewalls and a ···
Contents
1 Description 1
. . . . . . . . . . . 1
. . . . . . . . . . . 2
2 Overview Of Lab Tasks
2.1 Iptables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
2.2 Nmap. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2.3 Snort. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
3 Submission 4
4 5
This assignment give students insight on how firewalls work by playing with network scanning, firewalls and a Network Intrusion Detection and Prevention system. In this assignment we will use Nmap for scanning and we will focus on Network Based Firewall and Host Based Firewall. Network Based Firewall filters traffic going from Internet to secured LAN and vice versa, a host based firewall is a software application or suite of applications installed on a single computer and provides protection to the host.
1 Description COMS3000/7003作业代写
1.1 Setting Up A Local Seed Lab environment
Students need to set up a local seed lab environment, please use image of SEED Ubuntu16.04 VM(32-bit):
1.Seed Labs Image Download
2. Seed Lab Setup Guide
Please consult the tutors in tutorials regarding issues regarding setting up a local seed lab environment
1.2 Your Tasks COMS3000/7003作业代写
1.Using iptables (Host-BasedFirewall)
(a)PreventMachine A doing telnet to Machine B
(b)PreventMachine A being telnet from Machine B
(c)PreventMachine A from accessing an external website
(d)PreventMachine A response to ICMP (Ping) requests
2.UsingNmap to perform scanning and use three different Nmap flags (e.g. flags for normal scan, udp scap, xmas scan, ) to perform three different types of scanning
3.Writing Snort Rules (Network-Based Firewall)to
(a)Alertscanning corresponding to each type of scans in your Nmap task (3 Snort rules)
(b)Alertwhen local machine tries to access http://staff.uq.edu.au
(c)SSH brute force attackalerting
2 Overview Of Lab Tasks COMS3000/7003作业代写
2.1 Iptables
Linux has a tool called iptables, which is essentially a firewall. In this task, the objective is to use iptables to set up some firewall policies, and observe the behaviors of your system after the policies become effective. You need to set up at least two VMs, one called Machine A, and another called Machine B. You run the firewall on your Machine A. Essentially, we use iptables asa personal firewall for host A. You can find the manual of iptables by typing “maniptables” or search it online. We list some commonly used commands in the following:
# List all the rules in the filter table sudo iptables -L sudo iptables -L --line-numbers # Delete all the rules in the filter table sudo iptables -F # Delete the 2nd rule in the INPUT chain of the filter table sudo iptables -D INPUT 2 # Drop all the incoming packets that satisfy the <rule> sudo iptables -A INPUT <rule> -j DROP
2.2 Nmap COMS3000/7003作业代写
Nmap is used to discover hosts and services on a computer network by send- ing packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and op- erating system detection. You can find the manual of iptables by typing “man nmap” or searching online. We list some commonly used commands in the following:
# scan for port 22 within a CIDR range nmap -p 22 192.168.137.0/24 # scan for the os info nmap -o 192.168.43.101
You are required to experiment with three different types of Nmap scans (e.g. flags for normal scan, udp scap, xmas scan, etc.).
2.3 Snort
Snort is an open-source network-based intrusion detection/prevention sys- tem (IDS/IPS), it has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching and matching. You can install Snort in Seedlab via command:
sudo apt-get install snort
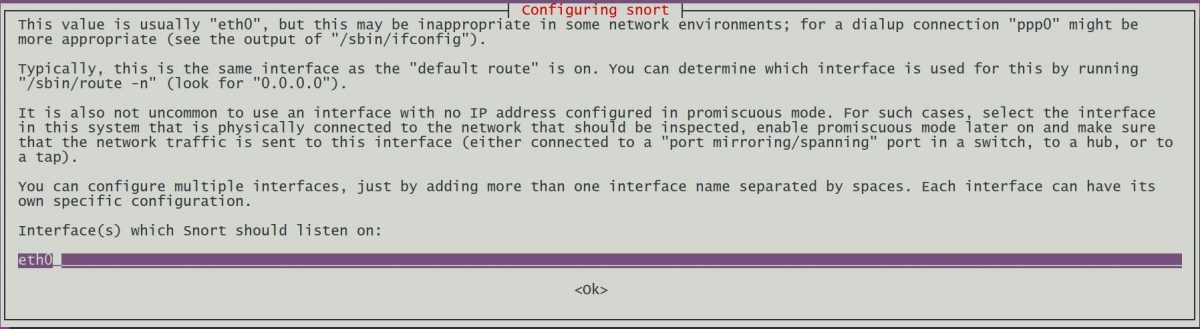
During the installation, Snort requires the name of the network interface. (See screenshots below) The network interface name may be different on your machine. It can be identified via the command: ifconftg, so in this case we should modify eth0 to enp0s3.
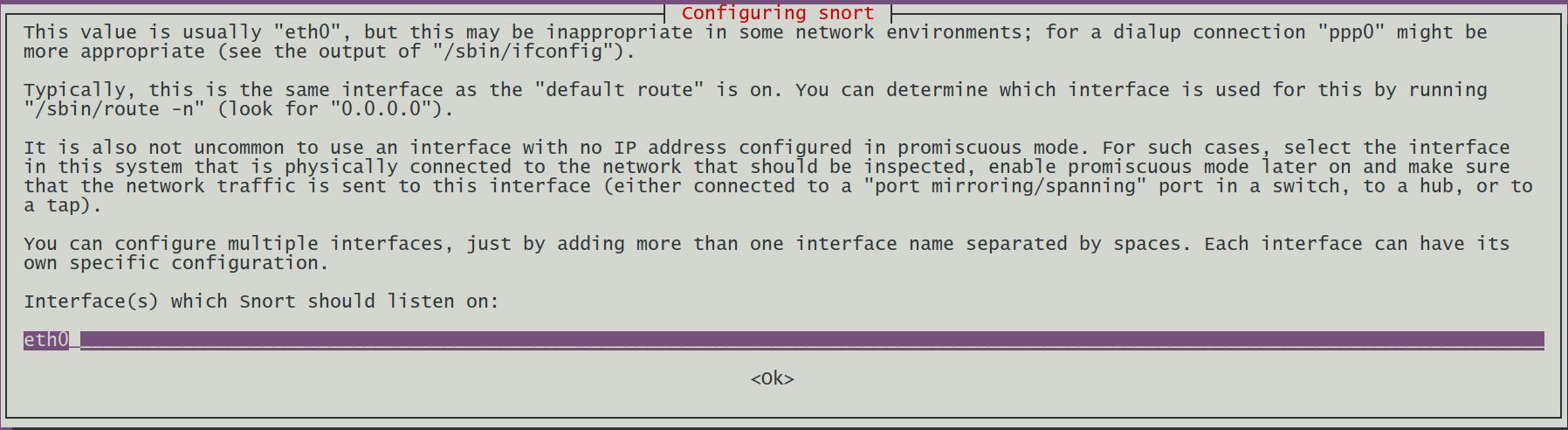
Figure 1: Snort Installation
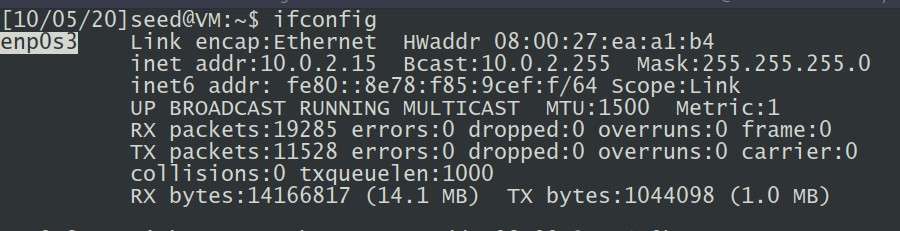
Figure 2: Get Correct Network Interface
This task depends on Nmap task, for example, if the Nmap tasks con- tains A, B, C, three types of scanning, the snort rules should corresponding to detecting and alerting A, B, C three types of scanning. Besides the 3 types of Nmap scanning detection, you are also required to write two additional snort rules:
1. Alert “Warning: This machine trying to access staff.uq.edu.au”
whenever machine A (running snort) tries to access http://staff.uq.edu.au
2.Alert against SSH Brutal Force Alert when external ma- chines fail 5 SSH logins to local machine A within 120seconds.
In order to finish this task, you need to modify the rules in snort con- figuration, to get familiar with these concepts, please refer to Snort User Manual
Snort demonstration will also be included in tutorials
3 Submission COMS3000/7003作业代写
- Fortask Iptable, your report needs to include the complete command, screenshots of before applying the relative iptable commands as well as screenshots after applying the iptable commands as well as your description of the iptable commands
- Fortask Nmap, your report needs to include the complete command, screenshots of your scanning results as well as your description about the nmap commands
- For task Snort, your report needs to include the snort rules, screen- shots of the running snort, as well as your description of the snort rules
4 Assessment COMS3000/7003作业代写
- Iptables (20marks)
– Prevent Machine A doing telnet to Machine B (5marks)
– PreventMachine A being telnet from Machine B (5 marks)
– PreventMachine A from accessing an external website (5 marks)
– PreventMachine A response to ICMP(Ping) requests (5 marks)
- Nmap Scanning (15marks)
– Threetypes of different scanning, 5 marks each
- Snort Detection (25marks)
– threetypes of different Nmap detection, 5 mark each
– Alert accessing staff.uq.edu.au (5marks)
– Alertagainst SSH brutal-force attacks (5 marks)
Total Marks: 60

其他代写:CS代写 assignment代写 homework代写 Exercise代写 algorithm代写 analysis代写 app代写 assembly代写 C++代写 C/C++代写 code代写 course代写 Data Analysis代写 data代写 essay代写