COMS3000 Information Security
COMS3000代写 Question 1. [9 marks] Describe each of the three primary tenets of information security that make up the so called “CIA-triad” and ···
Useful Information:
ALE = ARO x SLE
Complementary probability P(¬A) = 1- P(A)
Complementary probability P(B|A) = 1 – P(¬B|A)
Complementary probability P(¬B|¬A) = 1 – P(B|¬A)
Conditional probabilities P(A|B) = P(A ∩B) / P(B)
Conditional probabilities P(A ∩ B) = P(A) P(B|A)
Theorem of total probabilities P(B) = P(B|A) P(A) + P(B|¬A) P(¬A)

Question 1. [9 marks] COMS3000代写
Describe each of the three primary tenets of information security that make up the so called “CIA-triad” and give an example of how information security can be compromised in regards to each of these three primary tenets.
Question 2. [6 marks]
Classify each of the following controls as a Preventative, Detective or Reactive measure and explain why each is so classified:
“Review logs and security events for all system components to identify anomalies or suspicious activity.”
“Implement a formal security awareness program to make all personnel aware of the cardholder data security policy and procedures.”
“Implement an incident response plan.”
Question 3. [10 marks] COMS3000代写
The ABC company has suffered three extensive virus outbreaks on its internal networks in the last five years. The total costs to ABC for each of these three events were $16000, $8000 and $12000, respectively, in lost time and effort to recover.
a) [4 marks] Given this information, what is the Annualised Rate of Occurrence (ARO), Single Loss Expectancy (SLE) and Annualised Loss Expectancy (ALE)?
b) [6 marks] A vendor has proposed a new anti-virus solution that will cost $4200 per annum in licence and maintenance fees and is estimated to reduce the probability of a virus outbreak to just one in nine years – provide the figures for the proposed cost and benefit to show if this is or is not a more cost-effective solution.
Question 4. [5 marks] COMS3000代写
Explain what Residual Risk is and how it is calculated in quantitative risk analysis.
Question 5. [6 marks]
Describe and explain with examples, the difference between the three different factors of authentication.
Question 6. [5 marks] COMS3000代写
Explain how you could use certificate-based authentication to provide a practical two-factor authentication system? Ensure you explain how it achieves two-factor authentication.
Question 7. [2 marks]
Given an ideal (“random oracle model”) cryptographic hash function h() with 8-bit output, what is the probability of a collision from two randomly selected 128-bit inputs?
Question 8. [17 marks] COMS3000代写
A password system uses the “Slapdash Hashing Algorithm 9 (SHA-9)” that works as follows:
All punctuation, numerals, special characters and whitespace are discarded; all remaining text is converted to uppercase; all ‘W’s are converted to ‘UU’; all ‘Z’s are converted to ‘S’; then the first eight characters are converted to binary using the following code:
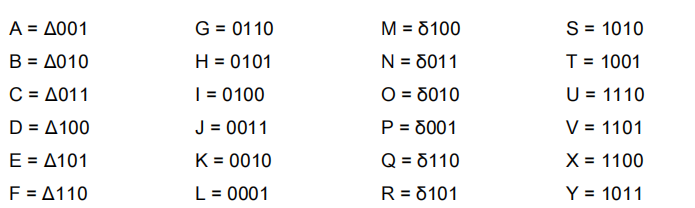
Where Δ is the salt (0 or 1) and δ is the binary inverse of Δ.
There is only one round in this algorithm. The result is output as nine hexadecimal characters consisting of the salt (0 or 1) followed by the 32-bit hash output as eight hexadecimal characters.
e.g. Password “password” may be recorded as “091AAEEAD” or as “119AAEE25”
a) [1 mark] What is the salt used for?
b) [2 marks] What does the password “ZuluDawn” get recorded as for a salt of 0?
c) [2 marks] What does the password “ZuluDawn” get recorded as for a salt of 1?
d) [2 marks] User Alice has password entry “1A2A4A95D”. Someone attempts to login as Alice and gives the password “BobIsThe14me” – will this validate correctly against “1A2A4A95D” and allow access?
e) [5 marks] Demonstrate, using only letters and ignoring case, a break of strong collision resistance for this hashing algorithm.
f) [5 marks] Using the password “AliceForever”, which hashes to “0114356AD” for salt “0”, using only letters and ignoring case, demonstrate a break of weak collision resistance of this algorithm.
Question 9. [5 marks] COMS3000代写
The MD5 and SHA-1 cryptographic one-way hash functions are no longer considered secure for a number of cryptographic applications. Explain what general cryptographic applications you could still currently rely on each of MD5 and SHA-1 and why you could still rely on these algorithms in those situations.
Question 10. [15 marks]
Consider a biometric system with the following (somewhat unrealistic) conditional probability density functions for the matching score S for an impostor and a genuine user.
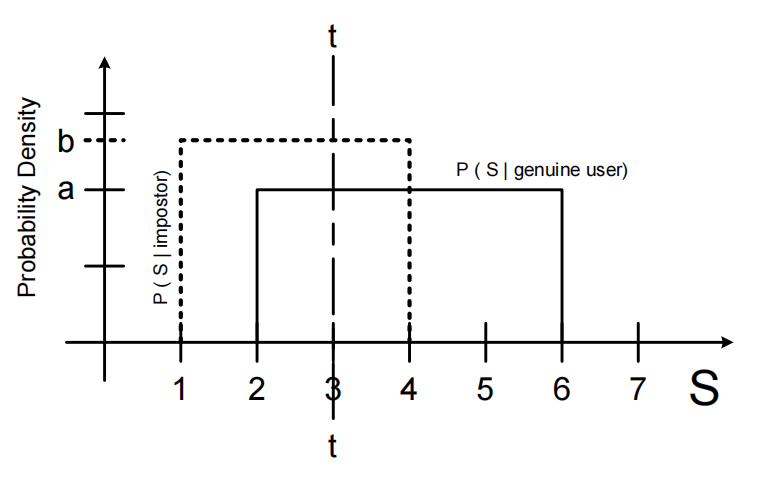
a) [3 marks] Calculate the parameters FAR and FRR.
b) [2 marks] What is the minimum realistic operational threshold t for which FAR = 0? What is the corresponding FRR for this value of t?
c) [3 marks] You are asked to adjust the system so that FAR=5%. Where do you need to set the threshold t to achieve this? What is the resulting FRR?
d) [7 marks] What is the Crossover Error Rate of the system?
Question 11. [15 marks] COMS3000代写
Consider a language consisting only of the following words with the corresponding probabilities:
Γ: p=0.25
Δ: p=0.10
Ξ: p=0.20
Σ: p=0.05
Θ: p=0.40
a) [6 marks] What is the average Shannon Information per word of text in this language?
b) [3 marks] The following binary encoding scheme is used for the above language.
Δ = 1
Θ = 00
Ξ = 010
Γ = 0110
Σ = 0111
Encode the following words of the language into a continuous bit stream: Δ Σ Γ Δ Θ Is this encoding unambiguous? (Explain why.)
c) [4 marks] What is the average number of bits required to encode a word using this encoding scheme?
d) [2 marks] How much redundancy does a code word contain on average?
Question 12. [5 marks] COMS3000代写
The ciphertext “EHZDUHWKHLGHVRIPDUFK” was produced with a “Caesar cipher”
using Julius Caesar’s historical key (according to Suetonius) and our modern 26-letter
alphabet. Correctly decrypt the ciphertext using any method.
Question 13. [10 marks]
Answer the following with regard to IPSec:
a) [2 marks] Explain why IPSec needs a security association (SA)?
b) [2 marks] Briefly explain how SPD and SAD in IPSec work.
c) [6 marks] Draw a figure to show an ESP packet created in transport mode. You need to include the following labels in your figure: IP header, transport header, and payload. Also, explain what information is encrypted and/or authenticated.
Question 14. [10 marks] COMS3000代写
Answer the following with regard to IDS and IPS:
a) [2 marks] Appraise the two main advantages of using host-based IDS compared to network-based IDS?
b) [4 marks] Compare and contrast signature-based intrusion detection techniques with anomaly-detection-based intrusion detection techniques?
c) [2 marks] We have discussed detection accuracy of intrusion detection systems. Which of false positive or false negative is more critical to the system? Explain why?
d) [2 marks] Briefly compare IDS and Intrusion Prevention Systems (IPS).

其他代写:CS代写 Data Analysis代写 data代写 澳大利亚代写 作业代写 report代写 paper代写 code代写 algorithm代写 作业加急 北美代写 essay代写 assignment代写 analysis代写 homework代写 加拿大代写 英国代写
