DESCRIPTION OF COURSEWORK
Course Code:SOF203
Coanse Name:Fundamemtal of Network Technology
Acdemic Session: 202304
Assessment Title: Assigment 2
网络技术基础代写 Plagiarism is submitting or presenting someone else’s work, words, ideas,data or information as your own intentionally or unintentionally.
A. Introduction/ Situation/ Background Information 网络技术基础代写
In this assignment, we’ll use variable length subnet mask (VLSM) in the subnet planning organization. We’ll then setup and configure a simple network with multiple Layer 3 switch.
B. Course Learning Outcomes (CLO) covered
At the end of this assessment, students are able to:
CL04: Perform planning and configuration for a simple network.
C. University Policy on Academic Misconduct
1. Academic misconduct is a serious offense in Xiamen University Malaysia. It car
as any of the following:
i. Plagiarism is submitting or presenting someone else’s work, words, ideas,data or information as your own intentionally or unintentionally. This includes in published and unpublished material, whether in manuscript, printed or electron published and unpublished material, whether in manuscript, printed or electron form into your work without acknowledging the source (the person and the work).
ii. Collusion is two or more people collaborating on a piece of work (in part or whole) which is intended to be wholly individual and passed it off as own individual work. 网络技术基础代写
iii. Cheating is an act of dishonesty or fraud in order to gain an unfair advantage in an asssment. This includes using or attempting to use, or assisting another to use materials that are prohibited or inappropriate, commissioning work from a third party, falsufying data,or breaching any examination nules.
2. All the asessment submitted must be the outcome of the student. Any form of scademic misconduct is a serious offense which will be penalised by being given a zero mark for the entire asessment in question or part of the assessment in question, If there is more than one guilty party as in the case of ollusion, both you and your ollusio purtner(s) will be subjected to the same penaly.

D. Instruction to Students 网络技术基础代写
1. This is an individual assignment.
2. Submit a softcopy of the assignment reporn to the Moodle system. You shouki submit together with a cower page containing your name and ID mumber. Please save your report as“A2-YourlD-Name”(without the double quotes, for example, A2-DMT1234567-YauWeiChuen.pdD and uploud the PDF file for your submission.
3. Your report should use the following formats:
- Alignment: Jutifed
- Font size: 12 points
- Font type: Times New Roman 网络技术基础代写
4. Compress all the eNSP files saved in Task 2 as “YourStudentID.ip” (e.g.. DMT1234567.zip).
Upload the zip fle on Moodle.
5. Submission deadline: 07 July 2022 (Thursday), before 12:00 noon.
6. Late submissions will be penalised,
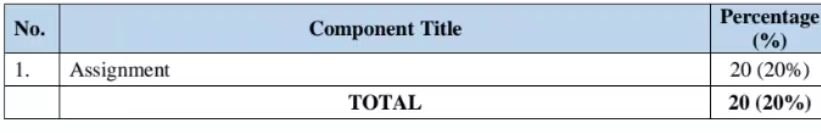
E. Evaluation Breakdown
F. Tasks
Your organization is allocated a block of address 10.Y.0.0/23. You are required to plan the subnetsand IP addressing based on the following address allocation requirement for each subnet as shown in Figure 1.
- The SWE LAN requires i5 addresses.
- The DMT LAN requires j5 addresses.
- The AI LAN requires k5 addresses.
- The EE LAN requires 12 addresses.
- The HR LAN requires 22 addresses.
- The Admin LAN requires 32 addresses
- Each link segment between two Layer 3 switches requires 2 addresses.
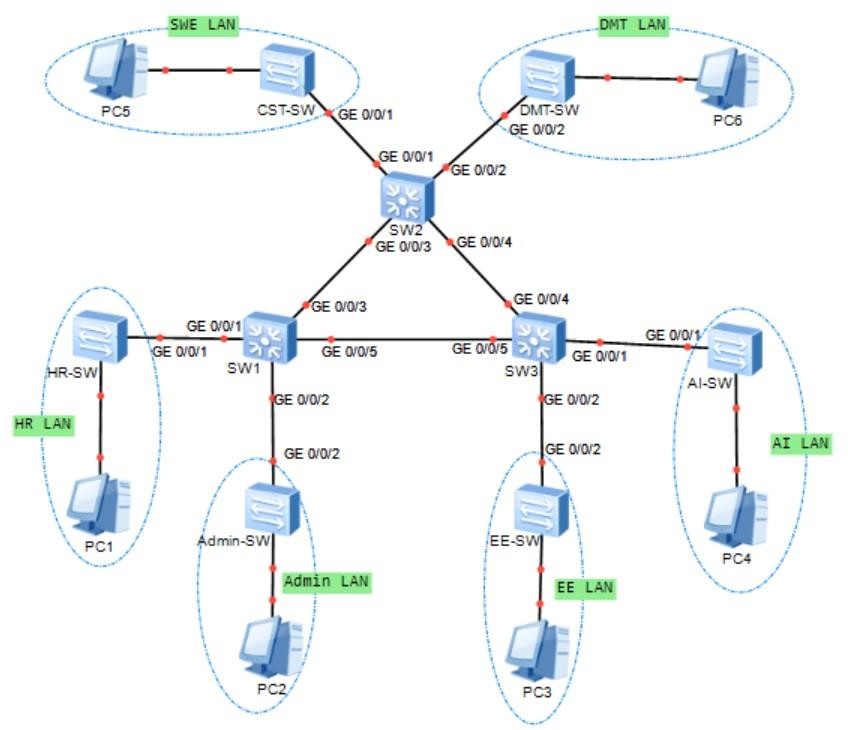
Figure 1
- Example 2: If your student ID is DMT2109100, the address block that you use in this assignment is 0.0.0/23. The SWE LAN requires 15 addresses. The DMT LAN requires 105 addresses. The AI LAN requires 105addresses.
Complete the following tasks.
Task 1. Subnet Planning and Layer 3 Switch Configuration 网络技术基础代写
- Perform subnet planning for your organisation’s network.
Show your work of subnet planning.
Assign VLAN ID and list the following address information for each subnet1:
- Network address
- Usable IP addressrange
- Broadcastaddress
- Decimal / CIDR Subnet mask
2.Table 1 is used for your configuration plan.
- Fill in the IP address and subnet mask for each of the PC and VLANIF’s interface.
3.Connect each device as shown in Figure1.
- Select “S5700” in eNSP as the Layer 3 switch for SW1, SW2, and SW3. (You can use S3700 if there is any issue of using S5700 with youreNSP)
-
- Use “S3700” in eNSP for the remaining switches in the diagram.
- You can select any appropriate switch’s interfaces for the link Make sure you perform your configuration on the correct interfaces in the subsequentsteps.
- Take a screenshot of your network topology. 网络技术基础代写
4.Rename the three “S5700” switches. You should configure it with your student ID followed by the device name as shown in Figure 1. For example, rename the switch SW1 as “DMT1234567-SW1” if your student ID is DMT1234567.
- Take a screenshot of your configuration on switch SW1. A sample is shown in Figure 2.
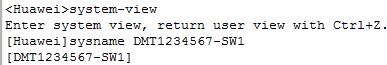
Figure 2
1 Do not assign VLAN 1 for your subnet.
4.Configure the switches with VLANs and assign IP addresses to the interfaces based on the results that you have obtained in Table 1.
- Take screenshots of your configuration on switchSW1.
- Take screenshots of your configuration on switchSW2.
- Take screenshots of your configuration on switchSW3.
6.Configure the PCs based on the results that you have obtained in Table 1.
- Take screenshots of your configuration on PCs.
Table 1
|
Device |
Interface (VLANIF) |
IP Address |
Subnet Mask |
Default Gateway |
|
SW1 |
– | |||
| – | ||||
| – | ||||
| – | ||||
|
SW2 |
– | |||
| – | ||||
| – | ||||
| – | ||||
|
SW3 |
网络技术基础代写 | – | ||
| – | ||||
| – | ||||
| – | ||||
| PC1 | – | |||
| PC2 | – | |||
| PC3 | – | |||
| PC4 | – | |||
| PC5 | – | |||
| PC6 | – |
Task 2: Dynamic Routes Configuration 网络技术基础代写
- DisableSTP on the interfaces connected between the three Layer 3 For example, you can enter the following command to disable STP on interface GE 0/0/3 of SW1 as shown in Figure 3.

Figure 3
- Configure RIP version 2 on each switch.
- Take a screenshot of your configuration on switchSW1.
- Take a screenshot of your configuration on switchSW2.
- Take a screenshot of your configuration on switchSW3.
- Verify the configuration by checking the routing table on each switch.
- Take a screenshot of the routing table on switchSW1.
- Take a screenshot of the routing table on switchSW2.
- Take a screenshot of the routing table on switchSW3.
- Use the pingcommand to verify the connectivity between the PCs. 网络技术基础代写
- Take screenshots of the ping result.
- Enter the tracert command to trace the route from PC2to
- Take a screenshot of the traceroute result.
6.Right-click the link between SW1 and SW3 and select “Remove Connection”. This will remove the link between SW1 and SW3 as shown in Figure 4.
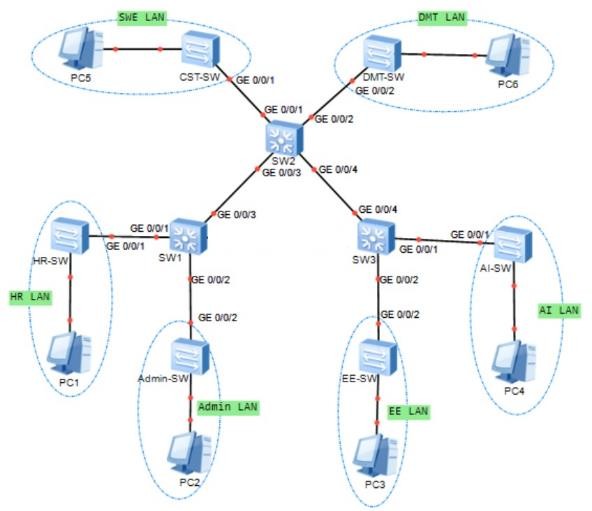
Figure 4
- Enter the tracert command again to trace the route from PC2 to
- Take a screenshot of the traceroute result.
- Checkthe routing table on SW1 and SW3 to observe the changes of the RIP route information.
- Take a screenshot of the routing table on switchSW1.
- Take a screenshot of the routing table on switchSW3.
- What are thechanges?
- Discuss your observation in Step 7 and 8. 网络技术基础代写
- Listat least two problems that you have faced during the configuration in task 1 and Discuss how you troubleshoot and solve the problems. Support your answer with appropriate screenshots. If you have not faced any problems during the configuration, discuss how you achieve it.
- Enter the “save” command to save the current configuration of switch SW1, SW2, andSW3 respectively.
- Saveyour work in eNSP by clicking on the “Save As” icon on the top left of eNSP’s menu bar.

