PROJECT 4: CASE STUDY 1 (CON’T) SECURITY PLAN AND RECOMMENDATION MEMO
案例研究代写 This information security plan is meant to establish and state the policies that govern Banking Solutions Inc.’s IT standards as well as practices.
This project involves the development of a Security Plan and a Recommendation Memo to the CIO. The plan communicates the security, policies, and the technologies being recommended from Projects 1, 2, and 3.
Information Security Plan
Executive Summery
This information security plan is meant to establish and state the policies that govern Banking Solutions Inc.’s IT standards as well as practices. The plan will protect the organization’s information and its critical data resources from possible threats. The main objective is to ensure the existence business continuity in the organization, minimize business risks, and maximize the organization’s return on investment including business opportunities. 案例研究代写
The information security will be achieved through the implementation of suitable controls, which include policies, security technology processes, procedures, hardware and software functions, and organizational structures. The controls have to be established and implemented, monitored and reviewed, as well as improved accordingly. This would ensure that the organization’s security, as one of the many business objectives, is achieved. This involves governing the privacy, security, as well as confidentiality of the organization’s data. All users of the organization are required to follow the Banking Solutions Inc. policies. It is also required that the organization’s employees maintain a shared responsibility regarding security of the organization’s information with respect to their departments.
译文:
信息安全计划 案例研究代写
执行摘要
该信息安全计划旨在制定和说明管理 Banking Solutions Inc. 的 IT 标准和实践的政策。该计划将保护组织的信息及其关键数据资源免受可能的威胁。主要目标是确保组织中存在的业务连续性,最小化业务风险,并最大化组织的投资回报,包括商业机会。
信息安全将通过实施适当的控制措施来实现,包括政策、安全技术流程、程序、硬件和软件功能以及组织结构。必须建立和实施控制措施,进行监测和审查,并相应地加以改进。作为众多业务目标之一,这将确保实现组织的安全性。这涉及管理组织数据的隐私、安全和机密性。该组织的所有用户都必须遵守 Banking Solutions Inc. 的政策。还要求组织的员工对其部门的组织信息安全负有共同责任。

Purpose
The main purpose of this security plan is to see that Banking Solutions maintains confidentiality, integrity, and data availability. The plan also will ensure that Banking Solutions defines, develops, and documents information policies as well as procedures supporting the goals and objectives of the organization. The plan also aims to allow Banking Solutions to satisfy responsibilities regarding the legal and ethical requirements with respect to the organization’s IT resources. The security policies and procedures stand for the organization’s foundation. Internal controls would provide a system of checks as well as balances meant for identifying irregularities, preventing waste, as well as fraud and abuse of information. 案例研究代写
译文:
目的
此安全计划的主要目的是确保 Banking Solutions 保持机密性、完整性和数据可用性。 该计划还将确保 Banking Solutions 定义、开发和记录信息政策以及支持组织目标的程序。 该计划还旨在使银行解决方案能够履行有关组织 IT 资源的法律和道德要求的责任。 安全政策和程序代表了组织的基础。 内部控制将提供一个检查和平衡系统,用于识别违规行为、防止浪费以及欺诈和滥用信息。
Scope
The plan will apply to whole organization including the management, employees, and other stakeholders. The key idea is to ensure data security. The information to be protected is typically part of the organization’s assets such as data, images, text, software, and related information resources whether stored online, on computers, or on paper among other storage media.
译文:
范围
该计划将适用于整个组织,包括管理层、员工和其他利益相关者。 关键思想是确保数据安全。 要保护的信息通常是组织资产的一部分,例如数据、图像、文本、软件和相关信息资源,无论是在线存储、存储在计算机上,还是存储在其他存储介质上的纸张上。
IT Governance Committee and Responsibilities
It governance is typically the management’s responsibility. It consists of aspects such as the leadership, the organizational structure, and the process for ensuring that IT sustains and extends the organization’s strategies and objectives. The management in this case will be responsible for the people to govern the information security and the strategic direction to be taken. It will ensure that the information security objectives are achieved accordingly. 案例研究代写
译文:
IT 治理委员会和职责 案例研究代写
它的治理通常是管理层的责任。 它包括领导力、组织结构以及确保 IT 维持和扩展组织战略和目标的过程等方面。 在这种情况下,管理层将负责管理信息安全和要采取的战略方向。 它将确保相应地实现信息安全目标。
The Organization’s Policy Statement
All departments within the organization will be obligated to protect the organization’s information resources. This will be done by implementing the security standards as well as procedures that are developed and approved by the government and the Information Security Board of Review. The organization’s departments will be required to meet all the minimum security standards. All departments would be encouraged to adopt the standards exceeding the minimum requirements. The information users will be responsible for complying with the general policies and their respective departments’ policies.
译文:
本组织的政策声明 案例研究代写
组织内的所有部门都有义务保护组织的信息资源。 这将通过实施安全标准以及政府和信息安全审查委员会制定和批准的程序来完成。 该组织的部门将被要求满足所有最低安全标准。 鼓励各部门采用超出最低要求的标准。 信息使用者将负责遵守一般政策及其各自部门的政策。
Enforcement
All users will be required to comply with both federal and state laws as well as the organization’s policies and procedures that govern the high-sensitive data security. Any user caught engaging in unauthorized access, use, alteration, destruction, or disclosure of data/information will be violating this plan and will be subjected to the appropriate disciplinary action such dismissal or legal action or even both.
译文:
执法 案例研究代写
所有用户都将被要求遵守联邦和州法律以及管理高敏感数据安全的组织政策和程序。 任何参与未经授权的访问、使用、更改、破坏或披露数据/信息的用户都将违反本计划,并将受到适当的纪律处分,例如解雇或法律诉讼,甚至两者兼而有之。
Information Security Program
Information security programs have been established, documented, and implemented. The programs are typically designed to improve IT operations effectiveness and ability to satisfy the existing regulatory requirements. The program is mainly set to ensure confidentiality as well as integrity of information within the organization. It is also meant to maintain an appropriate level of information and data accessibility. Three technological means have been put in place to ensure that information is protected from all reasonable forms of threat. The most technological/program measures include the use of firewall protection, use of remote access technology, and the use of account lockout technology/program (Avoyan, 2011). These technological means have both software and hardware components aimed at keeping information and related facilities secure. 案例研究代写
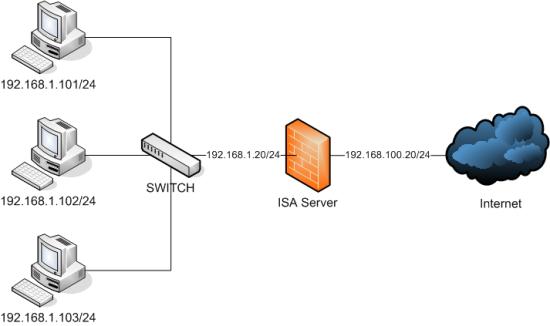
Regarding the firewall protection technology, the organization’s computers would be protected from internet threats by a firewall. An ISA Server is used to provide proxy firewall solutions to the organization. The firewall protection network diagram would be as shown in figure 1 below (Avoyan, 2011).
Firewall Protection Technology
Figure 1: Firewall Protection Network Diagram
译文:
信息安全计划 案例研究代写
信息安全计划已经建立、记录和实施。这些计划通常旨在提高 IT 运营效率和满足现有监管要求的能力。该计划主要是为了确保组织内信息的机密性和完整性。它还旨在保持适当级别的信息和数据可访问性。已经采用了三种技术手段来确保信息免受所有合理形式的威胁。大多数技术/程序措施包括使用防火墙保护、使用远程访问技术以及使用帐户锁定技术/程序(Avoyan,2011)。这些技术手段具有旨在确保信息和相关设施安全的软件和硬件组件。
关于防火墙保护技术,组织的计算机将通过防火墙保护免受互联网威胁。 ISA Server 用于为组织提供代理防火墙解决方案。防火墙保护网络图如下图 1 所示(Avoyan,2011)。
防火墙保护技术
图 1:防火墙保护网络图
Remote Access Technology
For the remote access technology, Banking Solutions Inc. would be able to control its users such that they can only connect to the internet from a specified remote location. This will allow the use of network resources, but at a controlled usage such that external threats are minimized. The same technology minimizes the risk of attackers gaining unauthorized access to the organization’s threats. The technology will enhance information security and allow user flexibility, even those willing to work from home (Microsoft, 2014). The remote access technology can be designed as shown in figure 2 below.
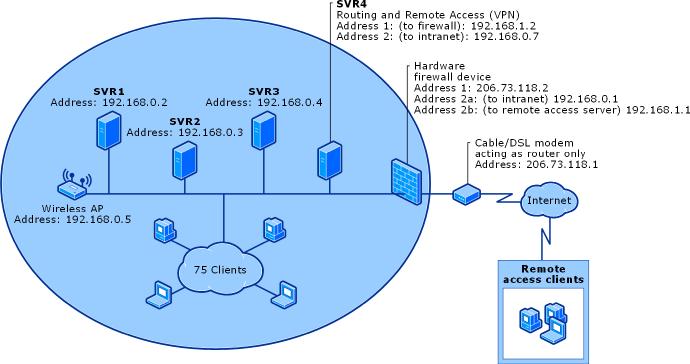
Figure 2: Remote Access Technology Network Diagram
译文:
远程访问技术
对于远程访问技术,Banking Solutions Inc. 将能够控制其用户,使他们只能从指定的远程位置连接到互联网。 这将允许使用网络资源,但以受控使用方式使外部威胁最小化。 相同的技术最大限度地降低了攻击者未经授权访问组织威胁的风险。 该技术将增强信息安全性并为用户提供灵活性,即使是那些愿意在家工作的人(微软,2014 年)。 远程访问技术可以设计如下图2所示。
图 2:远程访问技术网络图
Account Lockout and Password Technology Concept
This technology program would be important because the security of the organization’s information relies on the restriction level against unauthorized users. This program controls aspects like the number of possible login attempts, password length, password uniqueness, as well as password lifespan. Other than logon attempts, it prevents dictionary attacks, which involve the use of known words to try to access account information (Microsoft, Account Lockout and Password Concepts, 2004). Brute force attacks in which unauthorized users try all possible permutations, are prevented. Figure 3 describes the authentication process using the steps, which occur whenever logon attempts fail to work. 案例研究代写
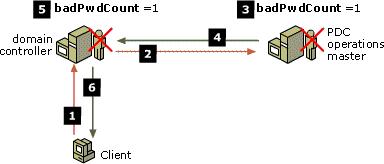
Figure 3: A Network Diagram for Failed Logon Attempt Process
译文:
帐户锁定和密码技术概念
该技术计划很重要,因为组织信息的安全性取决于对未经授权用户的限制级别。 该程序控制诸如可能的登录尝试次数、密码长度、密码唯一性以及密码寿命等方面。 除了登录尝试之外,它还可以防止字典攻击,这些攻击涉及使用已知词来尝试访问帐户信息(Microsoft,帐户锁定和密码概念,2004 年)。 防止未经授权的用户尝试所有可能的排列的蛮力攻击。 图 3 描述了使用这些步骤的身份验证过程,每当登录尝试失败时就会发生这些过程。
图 3:登录尝试失败过程的网络图
Associated Costs
The cost of ensuring security on the organizations information is relatively high. The cost would include installation cost for the three technologies, running costs, maintenance costs, and labor cost. The management will need to set a budget to meet these cost. 案例研究代写
译文:
相关成本
确保组织信息安全的成本相对较高。 成本将包括三种技术的安装成本、运行成本、维护成本和人工成本。 管理层需要制定预算来满足这些成本。
Risk Assessment
Risk assessment would be important to determine the vulnerability of the organization information to attacks. There is generally a high risk since Banking Solutions is a financial institutions with some online transactions and mode of payment. Besides, financial information is highly vulnerable to security attacks. The management can thus formulate effective strategies after an effective risk assessment (Microsoft, Account Lockout and Password Concepts, 2004).
译文:
风险评估 案例研究代写
风险评估对于确定组织信息对攻击的脆弱性非常重要。 由于 Banking Solutions 是一家具有一些在线交易和支付方式的金融机构,因此通常存在高风险。 此外,金融信息极易受到安全攻击。 因此,管理层可以在进行有效的风险评估后制定有效的策略(Microsoft,帐户锁定和密码概念,2004 年)。
Expected Return on Investment (ROI)
ROI would be the benefits resulting from the investment of security technologies. The technologies are likely to yield high ROI in which the investment gains would compare favorably to the investment costs. As long as risks and previous security problems will be eliminated, the technologies will result to increased profitability of the business. ROI will determine the plan effectiveness (Farris, Bendle, Pfeifer, & Reibstein, 2010). It will be computed as follows:
ROI = (Net profits / Investment Cost) × 100 案例研究代写
Where:
Net Profit = Gross Profits –Total Expenses
译文:
预期投资回报 (ROI) 案例研究代写
ROI 是安全技术投资所带来的收益。 这些技术可能会产生高投资回报率,其中投资收益与投资成本相比更为有利。 只要消除了风险和以前的安全问题,这些技术就会提高企业的盈利能力。 投资回报率将决定计划的有效性(Farris、Bendle、Pfeifer 和 Reibstein,2010 年)。 计算如下:
投资回报率 =(净利润 / 投资成本)× 100
在哪里:
净利润 = 毛利润 – 总费用
Recommendation Memo
MEMO TO: The CIO
FROM: Information Security Planner
DATE: October 25, 2014
SUBJECT: INFORMATION SECURITY PLAN FOR BANKING SOLUTIONS INC.
Banking Solutions Inc. is currently facing significant information security problems. The sensitivity of its business operations requires the use of highly secured information systems. An information security plan has been designed to help solve the problem. The plan incorporates three key technological security programs. These include firewall protection technology, account lockout technological process, and a remotely controlled access technology. A combination of these technologies would ensure that all possible threats to the organization’s information are mitigated.
The security plan will ensure that security on information is promoted with respect to the organization’s policies and government regulations. The main objective will be ensuring continuity of the business, minimizing information security risks, and maximizing the returns on investment (ROI). A close analysis has shown that although the investment cost would be relatively high, the financial benefits would be high. This is because the number of risks would be minimized greatly. 案例研究代写
Investors are likely to be attracted to the business because of the increased profitability and decreased risks of losses. This follows the fact that security controls would be in place to increase customer confidence as well. It is therefore recommended that the plan be reviewed the soonest possible in order to facilitate the necessary steps for implementation. It is also advisable to initiate any changes on the plan where necessary to perfectly meet the organization’s needs and budget especially given the prevailing changes within the business environment.
译文:
推荐备忘录 案例研究代写
致:首席信息官
来自:信息安全规划师
日期:2014 年 10 月 25 日
主题:银行解决方案公司信息安全计划
Banking Solutions Inc. 目前正面临重大的信息安全问题。其业务运营的敏感性需要使用高度安全的信息系统。已经设计了信息安全计划来帮助解决该问题。该计划包含三个关键的技术安全计划。其中包括防火墙保护技术、帐户锁定技术流程和远程控制访问技术。这些技术的组合将确保减轻对组织信息的所有可能威胁。
安全计划将确保根据组织的政策和政府法规促进信息安全。主要目标将是确保业务的连续性,最大限度地降低信息安全风险,并最大限度地提高投资回报 (ROI)。仔细分析表明,虽然投资成本会相对较高,但财务收益会很高。这是因为风险的数量将大大减少。
由于盈利能力的提高和亏损风险的降低,投资者很可能会被这项业务所吸引。这是遵循安全控制措施来增加客户信心的事实。因此,建议尽快审查该计划,以促进必要的实施步骤。还建议在必要时对计划进行任何更改,以完美满足组织的需求和预算,特别是考虑到业务环境中的普遍变化。
References 案例研究代写
Avoyan, H. (2011, August 17). How to Protect Your Network: Firewall Best Practices. Retrieved from blog.monitis.com: http://blog.monitis.com/2011/08/17/how-to-protect-your-network-firewall-best-practices/
Farris, P. W., Bendle, N. T., Pfeifer, P. E., & Reibstein, D. J. (2010). Marketing Metrics: The Definitive Guide to Measuring Marketing Performance. . Upper Saddle River, New Jersey: Pearson Education, Inc.
Microsoft. (2014, July 31). Account Lockout and Password Concepts. Retrieved from technet.microsoft.com: http://technet.microsoft.com/en-us/library/cc780271%28v=ws.10%29.aspx
Microsoft. (2014). Securing Remote Access. Retrieved from technet.microsoft.com: http://technet.microsoft.com/en-us/library/cc875831.aspx

其他代写:代写CS C++代写 java代写 matlab代写 web代写 app代写 作业代写 物理代写 数学代写 考试助攻 paper代写 论文代写 金融经济统计代写 python代写

